stick1977
Member
- Reaction score
- 0
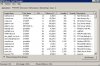
See attached, I don't get it. It's not just one process it's like 20 different processes all using a little bit of the processor.
One of the svchost.exe cycle eaters was associated with Event viewer so saved then cleared the logs. That actually helped for a bit but before long it was up to 100% again.
raw_agent_svc.exe is associated with the Datto box that's providing Business Continuity, I hope I don't have to spin that up due to this.
New server since July, PowerEdge T320 with 16 GB RAM, 8 core Xeon.
I've rebooted the Datto and have triggered an uninstall of AVG internet security business edition. Machine runs Exchange 2010 with about 30 mailboxes and is the file server.
Any recommendations would be great. Thanks so much in advance.
One of the svchost.exe cycle eaters was associated with Event viewer so saved then cleared the logs. That actually helped for a bit but before long it was up to 100% again.
raw_agent_svc.exe is associated with the Datto box that's providing Business Continuity, I hope I don't have to spin that up due to this.
New server since July, PowerEdge T320 with 16 GB RAM, 8 core Xeon.
I've rebooted the Datto and have triggered an uninstall of AVG internet security business edition. Machine runs Exchange 2010 with about 30 mailboxes and is the file server.
Any recommendations would be great. Thanks so much in advance.