Mike McCall
Well-Known Member
- Reaction score
- 1,073
- Location
- Silverton, Oregon
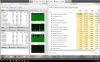
New client Zotac minipc Win 8.1. Signed them up for the residential monitoring, managed av, patch management, and web protection package. Device wouldn't pass the vulnerability scan. Couldn't connect to the database. I tried pinging update.microsoft.com and a couple others required for updates, and couldn't reach them. Then I ran tracert and it stopped at the same place you see below.Then an av scan found a virus and quarantined it. System dog slow, so I check Task Manager and find that the CPU is pegged at 100%. The main culprit is Windows Module Installer Worker. Apparently, TiWorker has been causing quite a few problems on 8.1 boxes. I tried stopping the service, but it continually restarted. I checked and both it and Windows update services were set to manual start. Ran sfc /scannow in safe mode as administrator, but got a message saying that it was unable to run, but no indication why. Finally, in safe mode I set both Windows Module Installer Worker, and Windows Update services to disabled to spare the CPU while I research this issue further.
Disabling those two services dropped the cpu usage to about 30%, but it remains steady with little fluctuation. Processes fluctuate, but total usage remains consistent. On the left in the screen capture below is the most recent tracert along side Task Manager. I tried running system restore in both normal and safe modes to no avail. I've run several scans for root kits or other malware and found nothing after the managed av found the virus (don't remember which one) and removed it. Uninstalled/reinstalled the monitoring agent, no change.
My thinking at this point is that either there's malware that I've yet to find, or there are corrupted files. I'm leaning toward the latter at this point. If I'm unable to work this out, I might suggest the client upgrade to 10 thinking it would correct whatever potentially corrupted files there are, as well as any software incompatibilities. So, what am I missing in this?
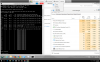
Disabling those two services dropped the cpu usage to about 30%, but it remains steady with little fluctuation. Processes fluctuate, but total usage remains consistent. On the left in the screen capture below is the most recent tracert along side Task Manager. I tried running system restore in both normal and safe modes to no avail. I've run several scans for root kits or other malware and found nothing after the managed av found the virus (don't remember which one) and removed it. Uninstalled/reinstalled the monitoring agent, no change.
My thinking at this point is that either there's malware that I've yet to find, or there are corrupted files. I'm leaning toward the latter at this point. If I'm unable to work this out, I might suggest the client upgrade to 10 thinking it would correct whatever potentially corrupted files there are, as well as any software incompatibilities. So, what am I missing in this?