britechguy
Well-Known Member
- Reaction score
- 4,021
- Location
- Staunton, VA
We all know that the only three truly safe sources for device drivers are the device OEM, your computer manufacturer's driver download pages, and Windows Update. But we also know that there are times where none of those get you what you need.
What has triggered this query is that I have an old Logitech QuickCam model V-UBG35. If you go to Logitech's site, and search on that model, you see that there is a page for it:
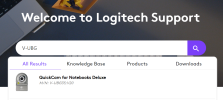
. . . but if you go to that page when you're browsing using Win11, you are told that there are no drivers for this version of Windows. OK, I know that, but I can then generally work my way backward by selecting Windows 10, Windows 8, etc., to look for the most recent one, but not on Logitech's site. And this seems to be happening more commonly now, and it drives me insane.
I've used Windows 7 and later drivers all the way up through Windows 11 for a number of older devices without a hitch. If the OEMs won't allow me to get to them, I occasionally need to source them elsewhere. But we also all know that there are scads of sketchy to utterly disasterous sources for device drivers.
So, when you find yourself in a pinch, what are the non-OEM sources you consider to be at least "reasonably safe?"
What has triggered this query is that I have an old Logitech QuickCam model V-UBG35. If you go to Logitech's site, and search on that model, you see that there is a page for it:

. . . but if you go to that page when you're browsing using Win11, you are told that there are no drivers for this version of Windows. OK, I know that, but I can then generally work my way backward by selecting Windows 10, Windows 8, etc., to look for the most recent one, but not on Logitech's site. And this seems to be happening more commonly now, and it drives me insane.
I've used Windows 7 and later drivers all the way up through Windows 11 for a number of older devices without a hitch. If the OEMs won't allow me to get to them, I occasionally need to source them elsewhere. But we also all know that there are scads of sketchy to utterly disasterous sources for device drivers.
So, when you find yourself in a pinch, what are the non-OEM sources you consider to be at least "reasonably safe?"
Last edited: