Metanis
Well-Known Member
- Reaction score
- 806
- Location
- Medford, WI, USA
I'm a slow learner!
Story: Small business customer got their sole Outlook.Com email account hacked. Of course, that's also their Microsoft Account. Customer was vague but I think they fell for the remote access Microsoft Tech Support popup.
Subsequently someone from Nigeria was replying to their legitimate email requests and trying to scam banking info from everyone they could. PS, their English was very good and they used complete sentences and even used my customer's cute little signature block. Here is a sample of the hacker's addition to an email thread trying to get a real customer's payment info:
So upon arrival, I ensured their single PC machine was no longer compromised and forced both major password changes and enabled 2-factor authentication on Microsoft and Google accounts. That was on Friday and on Monday my customer reported their email was still compromised.
What I didn't know was sad. Anyone with an EXISTING open session to Outlook.Com will remain authenticated UNTIL THEIR device closes the session!
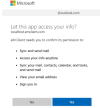
After some Google Fu I find the only option other than abandoning the email account is to navigate to user's Microsoft Account profile online and then drill into Security, then Advanced Security and find the option to "Sign Me Out". For some reason they claim it can take 24 hours to be effective!
I guess I haven't had to respond to enough hackers to be good at this stuff! Hopefully I've put the horse back in the barn for them.
Story: Small business customer got their sole Outlook.Com email account hacked. Of course, that's also their Microsoft Account. Customer was vague but I think they fell for the remote access Microsoft Tech Support popup.
Subsequently someone from Nigeria was replying to their legitimate email requests and trying to scam banking info from everyone they could. PS, their English was very good and they used complete sentences and even used my customer's cute little signature block. Here is a sample of the hacker's addition to an email thread trying to get a real customer's payment info:
Code:
Hi,
Please note: Henceforth we are unable to receive credit cards payments
or checks, payments are to be made electronically by Bank Transfer,
Zelle, CashApp.
Let me know your most preferable method of payment so i can have our
details sent to you for the balance payment.
~ Rosanna ~So upon arrival, I ensured their single PC machine was no longer compromised and forced both major password changes and enabled 2-factor authentication on Microsoft and Google accounts. That was on Friday and on Monday my customer reported their email was still compromised.
What I didn't know was sad. Anyone with an EXISTING open session to Outlook.Com will remain authenticated UNTIL THEIR device closes the session!
After some Google Fu I find the only option other than abandoning the email account is to navigate to user's Microsoft Account profile online and then drill into Security, then Advanced Security and find the option to "Sign Me Out". For some reason they claim it can take 24 hours to be effective!
I guess I haven't had to respond to enough hackers to be good at this stuff! Hopefully I've put the horse back in the barn for them.