Porthos
Well-Known Member
- Reaction score
- 12,532
- Location
- San Antonio Tx

Microsoft plans to kill malware delivery via Office macros
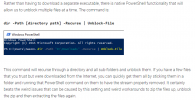
Microsoft announced today that it will make it difficult to enable VBA macros downloaded from the Internet in several Microsoft Office apps starting in early April, effectively killing a popular distribution method for malware.