Im trying to setup a guest wireless network for a client but they have a mish-mash of equipment and its giving me a headache!
The setup is this...
Billion 7800NXL router -> D-Link DGS-1100-24 switch -> Draytek 902 Access Point
So the first issue is the Billion router doesn't support VLAN tagging but it does have something called 'Interface Grouping' which is basically port based VLAN. So i have setup a guest group with DHCP on another subnet and attached port 2 on the router to it, then run two network cables to the switch.
View attachment 7310
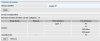
On the D-Link switch i set the following...
Default all ports - HYBRID VLAN ID 1 untagged
eth 2 (from port2 on router) - ACCESS VLAN ID 5 untagged
eth 5 (Access point) - HYBRID VLAN ID 1 untagged & VLAN ID 5 tagged
View attachment 7311
On the Draytek AP i created the following...
Wireless 1 - RPFoffice
Wireless 2 - RPFguest VLAN ID 5
View attachment 7313
The problem is it doesn't work, wireless clients connecting to guest seem to take forever to connect and then get an IP in the first LAN. Also, when i connect to the second LAN with a cable i have no internet as the WAN interface isnt part of the group on the Billion and it seems it can only be a member of one group?
Any ideas what im doing wrong?
Seems all Goofed up, and I think it is mostly from mismatched equipment but also from a lack of understanding of VLAN tagging vs untagged.
Looking at the Billion router, I see two Group ID's, yet I am not certain what functionality a group creates. Perhaps it is is like a firewall zone whereby to pass traffic from GuestNetwork to Default you need a rule/policy to allow said traffic?
I do notice you have both the LAN and WAN in the same Group. That would be akin to the same zone, which on a trusted network makes sense. Now for just plain routing, you would typically configure virtual interfaces on different VLANs; since, at Layer-3 the VLAN tags get stripped off anyway (i.e. for routing between subnets). That is that VLAN tags survive only within a any given Layer-2 network segment. None the less, it is still completely feasible to apply IP addresses at the Interface level regardless whether or not they are on different subnets, so having both your WAN and your LAN under Default is not necessarily wrong especially if these are really "zones."
Okay, now let's say that this router does not support VLANs. It would theoretically ignore any 802.1q tags and treat all tagged or untagged traffic as untagged traffic, so it would then not matter if the Interface facing it was tagged or untagged (i.e. trunk or access interface respectively). Best practice would be to ONLY face untagged interface(s) toward it.
What an untagged interface does is transmit/receive traffic where at layer-2 the VLAN tag field is blank within the Ethernet_II frame. It transmits and receives ONLY for traffic within the VLAN of which the interface is a member.
Hence, if your Billion router does NOT support VLAN's, you cannot trunk and therefore MUST use two separate network cables. One cable would be on P1 or P3 to the switch coming into an Untagged VLAN 1 interface. The other cable would be from P2 to any interface that is untagged on a different VLAN (i.e. VLAN5).
When that DLINK switch receives UNTAGGED frame(s) on an interface that is UNTAGGED to VLAN 5, those frames exist within memory on VLAN5 whereby they enjoy isolated ARP tables and perhaps Per-VLAN-Spanning-Tree(+) if so equipped. The frame will ONLY be transmitted via other UNTAGGED interfaces within VLAN 5 or from an interface TAGGED to VLAN5. The difference being transmitted on a TAGGED to VLAN5 interface would cause it to leave teh DLINK with an 802.1Q tag.
I see where it says eth5 on that Dlink switch is TAGGED to VLAN 5 and UNTAGGED to VLAN 1. This is what Cisco and most vendors refer to as a Native VLAN. Just because this interface can talk on both VLANS does NOT cause it to convert between the two. That is to say if this port receives an individual Etherent_II frame with the 802.1q field NUL or empty it places that frame into VLAN 1 whereby if it receives a frame with the 802.1q field set to VLAN 5 it places that frame into VLAN 5.
Any given frame may be a member of only one VLAN. Any given interface can only only be untagged to only one VLAN but may be TAGGED to many VLANs.
***********
The wireless router has me confused because there is no VLAN 0; it is simply not allowed within 802.1q. You may have 1 to 4095 only. Let's assume 0 = default which is VLAN 1 otherwise contact the vendor and inquire.
I notice only the word UNTAGGED to VLAN 5. What this would mean is that the Interface is within Layer-2 segment space within the wireless AP or router's memory but that it is transmitting/reeving without an 802.1q tag. If that is the case, can you associate both SSIDs to different interfaces on the Wireless router to connect them to different switch interfaces?
If yes, split the switch logically into any two VLANs making them all access (UNTAGGED) ports. It doesn't even matter what two you use; since, you are merely making two logical switches. Hang each logical switch from the router with two Ethernet cables and connect the router with two cables via the VLANs to the router.
What is key to know is that if an UNTAGGED frame leaves a device it does NOT matter what VLAN it left... it has no information on the frame. If it then flows into another interface that accepts UNTAGGED frames it becomes a member of whatever VLAN that interface has membership.