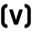autumn
Active Member
- Reaction score
- 26
- Location
- Geelong, Victoria, Australia
G day all from down under,
I had a client today ask if we can monitor a users usage. Not just internet but their programs, well everything they do. I know keyloggers is possible but I think they will want more. Does anyone use anything?
I'm using Atera for RMM, I haven't checked if they have a plug in that will do something that will help me.
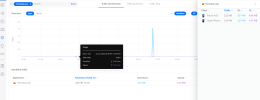
What's the reporting of websites in the Dream Machines like? Could a user easily access and read these?
I'll need to check the legalities here as well.
Of course they ask this when I'm heading off on holidays for 2 weeks.
I had a client today ask if we can monitor a users usage. Not just internet but their programs, well everything they do. I know keyloggers is possible but I think they will want more. Does anyone use anything?
I'm using Atera for RMM, I haven't checked if they have a plug in that will do something that will help me.
What's the reporting of websites in the Dream Machines like? Could a user easily access and read these?
I'll need to check the legalities here as well.
Of course they ask this when I'm heading off on holidays for 2 weeks.