i was speaking to Shadow Protect about this issue and they forwarded me a document related to this topic and too good not to share:
How to help prevent your computer from becoming infected by CryptoLocker and to help prevent ShadowProtect Images from being encrypted.
The first thing to do is change the share structure that ShadowProtect backs up to. Stop the old share and then create a new share called sharename$ like this \\servername\sharename$ with all server folders under this share. You then need to change the permissions on the share to only the service account being used by the ShadowProtect in its destinations - try to avoid using service credentials EG what account the ShadowProtect SVC is running under. There should only be the one account in the share permissions and do not use the administrators account.
Next follow the below to assist controlling the stupidity or lack of knowledge of the end-users.
You can use the Windows Group or Local Policy Editor to create Software Restriction Policies that block executables from running when they are located in specific paths. For more information on how to configure Software Restriction Policies, please see these articles from MS:
http://support.microsoft.com/kb/310791
http://technet.microsoft.com/en-us/library/cc786941(v=ws.10).aspx
The file paths that have been used by this infection and its droppers are:
C:\Users\<User>\AppData\Local\<random>.exe (Vista/7/8)
C:\Users\<User>\AppData\Local\<random>.exe (Vista/7/8)
C:\Documents and Settings\<User>\Application Data\<random>.exe (XP)
C:\Documents and Settings\<User>\Local Application Data\<random>.exe (XP)
In order to block the CryptoLocker you want to create Path Rules so that they are not allowed to execute. To create these Software Restriction Policies use the Local Security Policy Editor or the Group Policy Editor for a Domain.
How to manually create Software Restriction Policies to block CryptoLocker:
In order to manually create the Software Restriction Policies you need to be using Windows Professional or Windows Server. If you want to set these policies for a particular computer you can use the Local Security Policy Editor. If you wish to set these policies for the entire domain, then you need to use the Group Policy Editor and set this on the Default Domain Policy. Unfortunately, if you are a Windows Home user, the Local Policy Editor is not available. To open the Local Security Policy editor, click on the
Start button and type
Local Security Policy and select the search result that appears. You can open the
Group Policy Editor by typing Group Policy instead. In this guide we will use the Local Security Policy Editor in our examples.
Once you open the Local Security Policy Editor or the Default Domain Policy, you will see a screen similar to the one below.
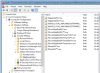
Once the above screen is open, expand
Security Settings and then click on the
Software Restriction Policies section. If you do not see the items in the right pane as shown above, you will need to add a new policy. To do this click on the
Action button and select
New Software Restriction Policies. This will then enable the policy and the right pane will appear as in the image above. You should then click on the
Additional Rules category and then right-click in the right pane and select
New Path Rule.... You should then add a Path Rule for each of the items listed below.
If the Software Restriction Policies cause issues when trying to run legitimate applications, you should see the end of this document on how to enable specific applications.
Below are a few Path Rules that are suggested you use to not only block the infections from running, but also to block attachments from being executed when opened in an e-mail client.
Block CryptoLocker executable in %AppData%
Path: %AppData%\*.exe
Security Level: Disallowed
Description: Don't allow executables to run from %AppData%.
Block CryptoLocker executable in %LocalAppData%
Path if using Windows XP: %UserProfile%\Local Settings\*.exe
Path if using Windows Vista/7/8: %LocalAppData%\*.exe
Security Level: Disallowed
Description: Don't allow executables to run from %AppData%.
Block Zbot executable in %AppData%
Path: %AppData%\*\*.exe
Security Level: Disallowed
Description: Don't allow executables to run from immediate subfolders of %AppData%.
Block Zbot executable in %LocalAppData%
Path if using Windows XP: %UserProfile%\Local Settings\*\*.exe
Path if using Windows Vista/7/8: %LocalAppData%\*\*.exe
Security Level: Disallowed
Description: Don't allow executables to run from immediate subfolders of %AppData%.
Block executables run from archive attachments opened with WinRAR:
Path if using Windows XP: %UserProfile%\Local Settings\Temp\Rar*\*.exe
Path if using Windows Vista/7/8: %LocalAppData%\Temp\Rar*\*.exe
Security Level: Disallowed
Description: Block executables run from archive attachments opened with WinRAR.
Block executables run from archive attachments opened with 7zip:
Path if using Windows XP: %UserProfile%\Local Settings\Temp\7z*\*.exe
Path if using Windows Vista/7/8: %LocalAppData%\Temp\7z*\*.exe
Security Level: Disallowed
Description: Block executables run from archive attachments opened with 7zip.
Block executables run from archive attachments opened with WinZip:
Path if using Windows XP: %UserProfile%\Local Settings\Temp\wz*\*.exe
Path if using Windows Vista/7/8: %LocalAppData%\Temp\wz*\*.exe
Security Level: Disallowed
Description: Block executables run from archive attachments opened with WinZip.
Path if using Windows XP: %UserProfile%\LocalSettings\Temp\*.zip\*.exe
Path if using Windows Vista/7/8: %LocalAppData%\Temp\*.zip\*.exe
Security Level: Disallowed
Description: Block executables run from archive attachments opened using Windows built-in Zip support.
How to allow specific applications to run when using Software Restriction Policies
If you use Software Restriction Policies, or CryptoPrevent, to block CryptoLocker you may find that some legitimate applications no longer run. This is because some companies mistakenly install their applications under a user's profile rather than in the Program Files folder where they belong. Due to this, the Software Restriction Policies will prevent those applications from running.
Thankfully, when Microsoft designed Software Restriction Policies they made it so a Path Rule that specifies a program is allowed to run overrides any path rules that may block it. Therefore, if a Software Restriction Policy is blocking a legitimate program, you will need to use the steps given above to add a Path Rule that allows the program to run. To do this you will need to create a Path Rule for a particular program's executable and set the Security Level to
Unrestricted instead of Disallowed as shown in the image below.
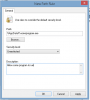
Once you add these Unrestricted Path Rules, the specified applications will be allowed to run again.
have attached as a PDF as well - Hopefully will be useful


