thecomputerguy
Well-Known Member
- Reaction score
- 1,453
I have a client who's owners are young whipper snappers and they will occasionally try to setup a new employee on an existing Azure joined device without involving me.
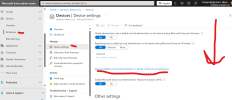
When you unbox a computer for the first time and Azure join it through Windows setup the initial account created is an Azure joined account with local admin privileges.
The issue is, if this employee is terminated and an additional Azure licensed account is added to the computer that next account is added as a standard user so can't install anything.
The original employees account is then decommissioned and now the computer has a local admin account that is not able to login, and a standard account that can't install anything.
I don't have my RMM on any of these systems, Non-MSP.
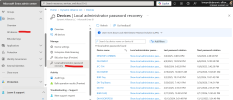
The only way I was able to get around it was to reinstate the original employees terminated local admin account, then use the command:
To promote the new user a local admin, then decommission the original account again. I then added a backdoor local admin account.
What can be done in the future to avoid this rudimentary process of regaining local admin without all of the above?
Yes I understand giving users local admin is not best practice but for small companies sometimes this is inevitable if they need to install a printer or something.
When you unbox a computer for the first time and Azure join it through Windows setup the initial account created is an Azure joined account with local admin privileges.
The issue is, if this employee is terminated and an additional Azure licensed account is added to the computer that next account is added as a standard user so can't install anything.
The original employees account is then decommissioned and now the computer has a local admin account that is not able to login, and a standard account that can't install anything.
I don't have my RMM on any of these systems, Non-MSP.
The only way I was able to get around it was to reinstate the original employees terminated local admin account, then use the command:
net localgroup administrators AzureAD\JohnDoe /add
To promote the new user a local admin, then decommission the original account again. I then added a backdoor local admin account.
What can be done in the future to avoid this rudimentary process of regaining local admin without all of the above?
Yes I understand giving users local admin is not best practice but for small companies sometimes this is inevitable if they need to install a printer or something.