- Reaction score
- 2,916
- Location
- Fort Myers, FL
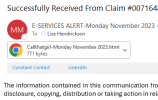
Client I setup last month with 365, security setup, all fine. Last Friday, her account started sending out a message about an e-services alert filing with html attachment.
She started hearing from people, who she didn't know, the usual. She has only 1 contact in her Exchange. I got the alert too after I looked, again I'm not in her database.
Today when I helped her, I found a lot of weird things going on. She did have a rule on for these e-service bounces to go to RSS, so I told her she was hacked. She swore up and down she never gave out her password. I can't find the original sent email anywhere nor in deleted.
Her admin center shows the hackers all over the world, so I told her she did get hacked somehow. Did all I could to stop that but we are now wondering if she didn't give it out, how did they get i and bypass the MFA?
In her devices we found her old Samsung tablet, that she never setup the new email on. But yet, there it was. I told her that I think her Gmail account with her 3 devices got compromised somehow. I read about something like this on Technibble last month, they are bypassing the text code and MFA somehow.
Any ideas?
She started hearing from people, who she didn't know, the usual. She has only 1 contact in her Exchange. I got the alert too after I looked, again I'm not in her database.
Today when I helped her, I found a lot of weird things going on. She did have a rule on for these e-service bounces to go to RSS, so I told her she was hacked. She swore up and down she never gave out her password. I can't find the original sent email anywhere nor in deleted.
Her admin center shows the hackers all over the world, so I told her she did get hacked somehow. Did all I could to stop that but we are now wondering if she didn't give it out, how did they get i and bypass the MFA?
In her devices we found her old Samsung tablet, that she never setup the new email on. But yet, there it was. I told her that I think her Gmail account with her 3 devices got compromised somehow. I read about something like this on Technibble last month, they are bypassing the text code and MFA somehow.
Any ideas?