thecomputerguy
Well-Known Member
- Reaction score
- 1,467
I have a client who I created a new tenant for and added their domain. We'll call the domain badinsurance.com
All email accounts were setup and they started using emails like john@badinsurance.com
Shortly after they discovered they were not allowed to use Bad Insurance or badinsurance.com for their company, the reasons don't matter.
So we registered goodinsurance.com
It seemed simple enough ... I added goodinsurance.com into the tenant, added DNS for MX, DKIM, DMARC, SPF, Autodiscover ... the usual. Added goodinsurance.com email addresses as Alias's then just swapped the primary email over to all of their goodinsurance.com emails.
We do not know if they experienced deliverability issues while using badinsurance.com - it was used sparingly. The company launched officially as goodinsurance.com
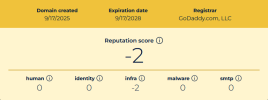
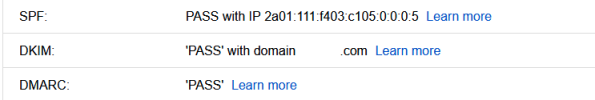
They are finding that they are having an issue with deliverability, inconsistently. For example I sent myself an email from a licensed account I have in their tenant for myself, to my Gmail and it went to spam even though everything passes ... see image below. That and everything passes here as well: https://www.learndmarc.com/
Of course when it comes to deliverability it's ultimately ends up in an IT game of finger pointing.
The only weird thing I can see is goodinsurance.com DKIM is authorized by badinsurance.com but I just popped whatever MS told me to pop into the DNS.
badinsurance.com
Host Name : selector1._domainkey
Points to address or value: selector1-badinsurance-com._domainkey.badinsurance.q-v1.dkim.mail.microsoft
Host Name : selector2._domainkey
Points to address or value: selector2-badinsurance-com._domainkey.badinsurance.q-v1.dkim.mail.microsoft
goodinsurance.com
Host Name : selector1._domainkey
Points to address or value: selector1-goodinsurance-com._domainkey.badinsurance.p-v1.dkim.mail.microsoft
Host Name : selector2._domainkey
Points to address or value: selector2-goodinsurance-com._domainkey.badinsurance.p-v1.dkim.mail.microsoft
SPF for Both: v=spf1 include:spf.protection.outlook.com -all
DMARC for Both: v=DMARC1; p=none;
HALP
All email accounts were setup and they started using emails like john@badinsurance.com
Shortly after they discovered they were not allowed to use Bad Insurance or badinsurance.com for their company, the reasons don't matter.
So we registered goodinsurance.com
It seemed simple enough ... I added goodinsurance.com into the tenant, added DNS for MX, DKIM, DMARC, SPF, Autodiscover ... the usual. Added goodinsurance.com email addresses as Alias's then just swapped the primary email over to all of their goodinsurance.com emails.
We do not know if they experienced deliverability issues while using badinsurance.com - it was used sparingly. The company launched officially as goodinsurance.com
They are finding that they are having an issue with deliverability, inconsistently. For example I sent myself an email from a licensed account I have in their tenant for myself, to my Gmail and it went to spam even though everything passes ... see image below. That and everything passes here as well: https://www.learndmarc.com/
Of course when it comes to deliverability it's ultimately ends up in an IT game of finger pointing.

The only weird thing I can see is goodinsurance.com DKIM is authorized by badinsurance.com but I just popped whatever MS told me to pop into the DNS.
badinsurance.com
Host Name : selector1._domainkey
Points to address or value: selector1-badinsurance-com._domainkey.badinsurance.q-v1.dkim.mail.microsoft
Host Name : selector2._domainkey
Points to address or value: selector2-badinsurance-com._domainkey.badinsurance.q-v1.dkim.mail.microsoft
goodinsurance.com
Host Name : selector1._domainkey
Points to address or value: selector1-goodinsurance-com._domainkey.badinsurance.p-v1.dkim.mail.microsoft
Host Name : selector2._domainkey
Points to address or value: selector2-goodinsurance-com._domainkey.badinsurance.p-v1.dkim.mail.microsoft
SPF for Both: v=spf1 include:spf.protection.outlook.com -all
DMARC for Both: v=DMARC1; p=none;
HALP