allanc
Well-Known Member
- Reaction score
- 387
- Location
- Toronto, Ontario, Canada
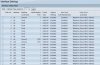
See attachment for my VLAN config.So the default VLAN1 includes ports 1 - 8 (excludes ports 9- 16)
If you want each client PC to be seperate, you need to place each one in a vlan.
So VLAN 1009 includes ports 1(tagged),9
VLAN 1010 includes ports 1(tagged), 10
Port 9 would have PVID set to 1009
Port 10 would have PVID set to 1010
Thats basically how mine is set up off the top of my head.
What router do you have?
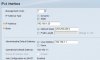
Right now, the computer on VLAN 1009 can not see VLAN 1010 (which is correct, it cannot see the router either.
Enabling PVID for port 1 on this screen does not resolve the issue.