britechguy
Well-Known Member
- Reaction score
- 4,851
- Location
- Staunton, VA
Received an email from a client a very short while ago with this screenshot, taken using her phone. Thank heaven she just stopped, dead, and did nothing other than take that photo and e-mail asking about it.
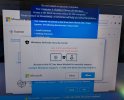
One of the most authentic looking versions of this kind of scam I've yet to run across. I gave her the step-by-step instructions for restarting and kicking off an immediate offline scan with the real Windows Defender, which I have every reason to believe will detect and remove this. Also told her if it shows up again we need to use a different malware removal tool.

One of the most authentic looking versions of this kind of scam I've yet to run across. I gave her the step-by-step instructions for restarting and kicking off an immediate offline scan with the real Windows Defender, which I have every reason to believe will detect and remove this. Also told her if it shows up again we need to use a different malware removal tool.