thecomputerguy
Well-Known Member
- Reaction score
- 1,435
Sorry about the length of this message...
I took on a new Insurance company the absorbed the original insurance company I worked with (they didn't have IT support). My client merged with this and is now double the size (25 users).
I'm not really sure what to do here.
I added most of my clients into this tenant with their new email addresses and forwarded everything from my original clients tenant to this new tenant (enabled external forwarding with auto-reply until we can eventually kill it).
New company gave me a global admin account so I could accomplish all of this.
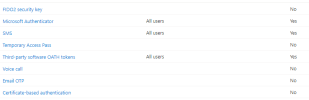
Prior to adding the emails a couple things I saw was that they had security defaults disabled, and they were using per user MFA (sorta). This also means legacy protocols are still enabled like POP, IMAP, and SMTP Auth. Their "admin employee" setup a couple of our users and I setup the rest. The ones I setup I enabled per user MFA because I wasn't about to botch the whole system since this turned into a "rush" merger and I was unfamiliar with the tenant. The "admin employee" did not enable per user MFA for a couple of our people.
Now I've gotten two phone calls of suspicious emails and I'm on a wild goose chase, especially being the "new" IT guy, and now I'm the one that gets to deal with this stuff, yay me.
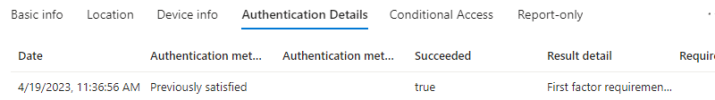
The 1st one was one of our people who did not have per user MFA enabled (I didn't set this user up). I did not see any bad sign-ins in Azure in this particular case but I changed the users password, enabled per user MFA and sent her off. Maybe I'm looking in the wrong place.
The 2nd one now is one of "their" people. Apparently she sent an email to a client, CC'd one of our people. Our people received the email correctly. The client received all of the correct header information, and even included our person in the CC but the reply to was changed to some spam email, and the body of the email was changed to a "you won a free gift card!".
Basically internally we see successful delivery of:
From: us@company.com
To: client@yahoo.com
CC: us2@company.com
Subject: Here is your quote
Body: Everything is fine
The client received:
From: us@company.com
To: client@yahoo.com
CC: us2@company.com
Replyto: spam@scammer.com
Subject: Here is your quote
Body: You won a free gift card!
We did not get CC'd on the spam email we received the CORRECT email at the CORRECT time.
The weird thing is I did a message trace and the message trace looks totally fine and was sent at 5:43PM from the correct person. The message trace shows NO indication of the spam email, unless I guess if it was somehow sent through SMTP invisibly?
The client forwarded the spam email to them, then they forwarded to me (in panic) and shows that the message was sent at 5:43PDT (so the exact same time) and I find that impossible.
It's almost like this email was intercepted in transit, and the body was changed, or the clients email is compromised and stripped and changed the body. This is a new one for me, I have no idea.... but the clients email is @yahoo.com
This happened about 5 days ago and there has been nothing done (I just heard about it), and there has been no further issue.
Bigger issues we have here are:
This sending user does not have per-user MFA enabled (along with about another 15 users).
The tenant does not have security defaults enabled.
Per-User MFA is not enabled for everyone.
POP, IMAP, SMTP are all still enabled for all users.
No DMARC
No DKIM
SPF is just the standard O365 record (v=spf1 include:spf.protection.outlook.com -all)
I feel like their client is the one compromised here. They re-forwarded the email to the client and he received it fine.
Beyond this issue what is the correct way to lock this thing up?
- Add the DKIM and DMARC records
- Disable per-user MFA for EVERYONE
- Reset everyone's password to a temp password and carrier Pidgeon it over to them
- Enable security defaults
- Re-do MFA across the board?
UGHHHHHHHHHH HALP IM LOSING MY MIND I DON'T HAVE TIME FOR A MERGER RIGHT NOW
@YeOldeStonecat @Sky-Knight
I took on a new Insurance company the absorbed the original insurance company I worked with (they didn't have IT support). My client merged with this and is now double the size (25 users).
I'm not really sure what to do here.
I added most of my clients into this tenant with their new email addresses and forwarded everything from my original clients tenant to this new tenant (enabled external forwarding with auto-reply until we can eventually kill it).
New company gave me a global admin account so I could accomplish all of this.
Prior to adding the emails a couple things I saw was that they had security defaults disabled, and they were using per user MFA (sorta). This also means legacy protocols are still enabled like POP, IMAP, and SMTP Auth. Their "admin employee" setup a couple of our users and I setup the rest. The ones I setup I enabled per user MFA because I wasn't about to botch the whole system since this turned into a "rush" merger and I was unfamiliar with the tenant. The "admin employee" did not enable per user MFA for a couple of our people.
Now I've gotten two phone calls of suspicious emails and I'm on a wild goose chase, especially being the "new" IT guy, and now I'm the one that gets to deal with this stuff, yay me.
The 1st one was one of our people who did not have per user MFA enabled (I didn't set this user up). I did not see any bad sign-ins in Azure in this particular case but I changed the users password, enabled per user MFA and sent her off. Maybe I'm looking in the wrong place.
The 2nd one now is one of "their" people. Apparently she sent an email to a client, CC'd one of our people. Our people received the email correctly. The client received all of the correct header information, and even included our person in the CC but the reply to was changed to some spam email, and the body of the email was changed to a "you won a free gift card!".
Basically internally we see successful delivery of:
From: us@company.com
To: client@yahoo.com
CC: us2@company.com
Subject: Here is your quote
Body: Everything is fine
The client received:
From: us@company.com
To: client@yahoo.com
CC: us2@company.com
Replyto: spam@scammer.com
Subject: Here is your quote
Body: You won a free gift card!
We did not get CC'd on the spam email we received the CORRECT email at the CORRECT time.
The weird thing is I did a message trace and the message trace looks totally fine and was sent at 5:43PM from the correct person. The message trace shows NO indication of the spam email, unless I guess if it was somehow sent through SMTP invisibly?
The client forwarded the spam email to them, then they forwarded to me (in panic) and shows that the message was sent at 5:43PDT (so the exact same time) and I find that impossible.
It's almost like this email was intercepted in transit, and the body was changed, or the clients email is compromised and stripped and changed the body. This is a new one for me, I have no idea.... but the clients email is @yahoo.com
This happened about 5 days ago and there has been nothing done (I just heard about it), and there has been no further issue.
Bigger issues we have here are:
This sending user does not have per-user MFA enabled (along with about another 15 users).
The tenant does not have security defaults enabled.
Per-User MFA is not enabled for everyone.
POP, IMAP, SMTP are all still enabled for all users.
No DMARC
No DKIM
SPF is just the standard O365 record (v=spf1 include:spf.protection.outlook.com -all)
I feel like their client is the one compromised here. They re-forwarded the email to the client and he received it fine.
Beyond this issue what is the correct way to lock this thing up?
- Add the DKIM and DMARC records
- Disable per-user MFA for EVERYONE
- Reset everyone's password to a temp password and carrier Pidgeon it over to them
- Enable security defaults
- Re-do MFA across the board?
UGHHHHHHHHHH HALP IM LOSING MY MIND I DON'T HAVE TIME FOR A MERGER RIGHT NOW
@YeOldeStonecat @Sky-Knight
Last edited: