HCHTech
Well-Known Member
- Reaction score
- 4,249
- Location
- Pittsburgh, PA - USA
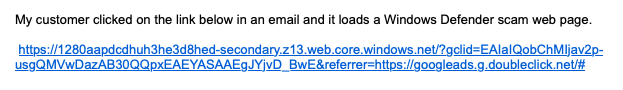
Got a ticket today from a client user - they couldn't open a spreadsheet that was sent to them encrypted via M365. My client is on Business Premium licenses, and 2FA is enabled tenant-wide.
The message came into her Outlook, and on trying to open the message, she got an M365 login box (we have their logo enabled on the M365 tenant, so I know this was a legitimate login request. She was already logged in to her Office apps, but once she logged in again in response to this request, she got a message that
"Your account is blocked - We've detected suspicious activity on your account. Sorry, the organization you are trying to access restricts at-risk users. Please contact your [company name] admin,."
There was a 'more details' link, which brought up this dialog:
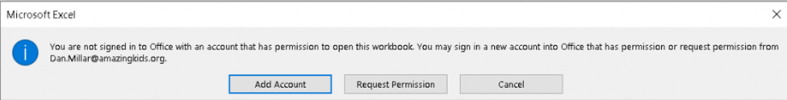
Then, finally, this dialog:
Logging onto the MS Entra admin center, and selecting "Risky activities", I do indeed see her username listed on the "Risky users" report. Status is "at risk". If I click on "User signins", I see many with status 'Success' and showing the town they are in under "Location". I also see a bunch of entries with status "Failure" from various locations in China, AE, Bengal, etc. I went through the entire list and all of the attempted logins shown for locations that weren't their office location have status "Failure". I'm presuming this means that none of these login attempts were successful.
If I choose to display just the "Risky signins", no entries are displayed.
If I choose to display "Users risk detections" I also get no entries.
Also, if you drill into the details of one of the failure entries, it says:
==========
Failure reason
Error validating credentials due to invalid username or password.
Additional Details
The user didn't enter the right credentials. It's expected to see some number of these errors in your logs due to users making mistakes.
==========
So I'm left wondering why a bunch of unsuccessful foreign logins (which have to happen for almost any address these days) put her in the "Risky User" category, and further what the right action to take is. Since there were no actual successful logins from abroad, I'm tempted to choose "Dismiss user(s) risk", which will likely fix the problem. I'm concerned however about how to determine the risk of doing this. It clearly says "Users can also have detections not linked to sign-in activity - To see all the detections, go to Risk Detections". Going there, however shows an empty list.
I see 2 other users on the risky users list as well, and the data for them looks similar, so they are NOT giving me much comfort either way.
The message came into her Outlook, and on trying to open the message, she got an M365 login box (we have their logo enabled on the M365 tenant, so I know this was a legitimate login request. She was already logged in to her Office apps, but once she logged in again in response to this request, she got a message that
"Your account is blocked - We've detected suspicious activity on your account. Sorry, the organization you are trying to access restricts at-risk users. Please contact your [company name] admin,."
There was a 'more details' link, which brought up this dialog:

Then, finally, this dialog:

Logging onto the MS Entra admin center, and selecting "Risky activities", I do indeed see her username listed on the "Risky users" report. Status is "at risk". If I click on "User signins", I see many with status 'Success' and showing the town they are in under "Location". I also see a bunch of entries with status "Failure" from various locations in China, AE, Bengal, etc. I went through the entire list and all of the attempted logins shown for locations that weren't their office location have status "Failure". I'm presuming this means that none of these login attempts were successful.
If I choose to display just the "Risky signins", no entries are displayed.
If I choose to display "Users risk detections" I also get no entries.
Also, if you drill into the details of one of the failure entries, it says:
==========
Failure reason
Error validating credentials due to invalid username or password.
Additional Details
The user didn't enter the right credentials. It's expected to see some number of these errors in your logs due to users making mistakes.
==========
So I'm left wondering why a bunch of unsuccessful foreign logins (which have to happen for almost any address these days) put her in the "Risky User" category, and further what the right action to take is. Since there were no actual successful logins from abroad, I'm tempted to choose "Dismiss user(s) risk", which will likely fix the problem. I'm concerned however about how to determine the risk of doing this. It clearly says "Users can also have detections not linked to sign-in activity - To see all the detections, go to Risk Detections". Going there, however shows an empty list.
I see 2 other users on the risky users list as well, and the data for them looks similar, so they are NOT giving me much comfort either way.
Last edited: