Unfortunately, no. Two out of the nine are. But the rest are not really close.
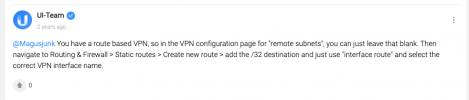
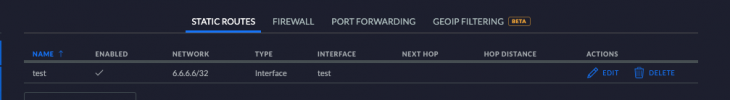
Earlier today I thought maybe I could simply create 9 static routes, one for each unique public IP. The route would send that traffic to the site-to-site interface. Kinda a crap shoot maybe.
Looks like this in the GUI
I sent this message to Flexential support on the open ticket:
"Could this be a valid way to solve this problem? Set up 9 static routes, 1 for each of the public IPs on the encryption domain. An example would look like this" (with the above screenshot attached)
Their response:
"To clarify our understanding you are asking us if setting up static routes on your firewall will bring this tunnel up? As previously stated we do not manage the remote firewall (your end) and cannot offer support on the Ubiquiti device. Our previous notes indicate you were working with Ubiquiti to come up with a solution of how the VPN tunnel should be set up on your side. Upon review the tunnel has been configured on our end and we are currently awaiting for you to complete the configurations on your side. If you need any further assistance please let us know."
Aaarrrggghhhh!!!!