britechguy
Well-Known Member
- Reaction score
- 5,110
- Location
- Staunton, VA
Still cannot get Ventoy to work for me, and that's using brand spankin' new thumb drives, too.
I've run Ventoy 1.1.07 to format the thumb drives. I've tried MBR and GPT, as well as exFAT, NTFS, and FAT32 file system formats. Regardless of the combination, after I've dragged and dropped several ISO files to that drive, this is what I get when I attempt to boot from any of them:
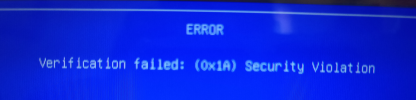
I have no idea what's wrong at this point. I have no problem booting from USB media I've created with Rufus or Balena Etcher.
I've run Ventoy 1.1.07 to format the thumb drives. I've tried MBR and GPT, as well as exFAT, NTFS, and FAT32 file system formats. Regardless of the combination, after I've dragged and dropped several ISO files to that drive, this is what I get when I attempt to boot from any of them:

I have no idea what's wrong at this point. I have no problem booting from USB media I've created with Rufus or Balena Etcher.
