normbarb
Member
- Reaction score
- 0
- Location
- Gainesville, VA
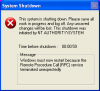
Norm - Out of interest, how do you know it is being caused by a virus?
Have you tried to stop it running with rkill?
Or, if you can get it running in 60 secs you could try Process Explorer to suspend (not shut down) the process it relies on.
Failing that I'd be looking to edit the registry and delete the relevant startup entries.
I don't know what else would cause this pop up saying it will shut down in 60 seconds, other than a virus.
RKill causes the pop up to appear and the computer shuts down.
Process Explorer: I can shut down processes, reg key, etc, but never found the one that causes the problem. No matter what I shut down, I would still get the 60 second pop up and shutdown when I tried to scan.
Dr Web, which boots it in Linux and does a scan, says it is Backdoor Trojan. Still scanning, so not sure if I can kill it.
Norm