- You are here:
- Home »
- Blog »
- Manage Your Computer Business »
- Fighting the Good Fight: An Interview with Malwarebytes Founder Marcin Kleczynski

Fighting the Good Fight: An Interview with Malwarebytes Founder Marcin Kleczynski
If you’re involved in serious malware removal these days, chances are that Malwarebytes has a soft spot in your heart. Technicians around the world (including my own company) have been combating “virtual gunk” on customer PCs with the help of Malwarebytes Anti-Malware since its first release back in 2008.
At my previous IT job, there were instances where Malwarebytes was the only tool that could handle specific wide-scale infections. So when the company’s founder Marcin Kleczynski agreed to chat, it was the opportunity of a lifetime for me. We discussed a range of topics including the current state of malware, where its headed in 2013, and how the future of Malwarebytes’ software is shaping up for the foreseeable future.

The Malwarebytes Front Office
Seeing as Marcin had a recent, lengthy interview with TechSpot that went in depth about the history of Malwarebytes and their success story, we’re not going to beat a dead horse there. You can read what he had to say to TechSpot on your own. I had a lot of questions that many techs may be more curious in, which he had no problems divulging his opinion about. I’m glad I was fortunate to catch the busy CEO on a light work day!
Derrick Wlodarz: Where do you feel that Malwarebytes Anti-Malware fits on a modern PC? In combination with another AV product, or as the sole protection solution?
Marcin Kleczynski: The simple answer is that it’s meant to work in combination with another AV product. The product [Malwarebytes Anti-Malware] was designed about 4 years ago when my antivirus had actually failed me. I was a victim of malware. I found a forum where there were hundreds of other people who were in the same boat. Even though they claim they do it all, antivirus software simply cannot.
Very quickly, we realized that zero day threats that are polymorphic in nature were simply too much for regular AV software, and there had to be some sort of stopgap solution. That’s where we came up with the Anti-Malware product. We wanted to plug those holes. We aren’t looking to necessarily replace your current antivirus product; we’re looking to supplement it.
Derrick: How long has Malwarebytes been around as a company?
Marcin: We were developing freeware until about 2006, and in 2007 I started writing the first version of the Anti-Malware engine. In 2008, we released the first true version of the product to the public. So while the program itself has only been available for about 4 years, the company has been in existence for about 8 years.
Derrick: In your interview with TechSpot, there was mention of a product called RogueRemover. Is that a product that you made? Or was it one of your friends?
Marcin: It was actually a friend and I. He took care of the database aspect, and it was the predecessor to the Anti-Malware product. It served as the framework for Anti-Malware, which we built off of RogueRemover. Keep in mind that RogueRemover focused only on ransomware and rogue products, such as WinAntivirus 2007 and such. That’s what we really specialized in, and detected about 500 of those variants.
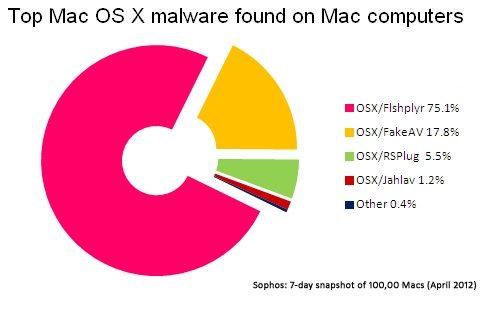
Derrick: This past summer, a Sophos study found that one in every 36 Macs has some form of malware installed. Does Malwarebytes have some solution to help address this problem for Mac users?
Marcin: Building a cross-compatible product for Mac and Windows is not a trivial matter; you can’t just port your Windows product to a Mac base. Fortunately, we do have a component called “malicious website blocking” that a Pro user can enable on their system. In essence, we have two components: file system blocking that prevents infection from malicious files, and the second one targets blocking connections to blacklisted IPs. These websites are ones that have either hosted malware in the past or are currently doing so.
The website blocking component is a lot easier to port because it works on a more standardized level that is common to both Macs and PCs. A malicious IP is the same whether you’re on a Windows or Mac system. So this component will likely be the one to get ported over in the future to any combination of platforms including possibly Linux, Mac, and mobile.
That being said, we hope to scale up in size and have a Mac research team that can detect these new threats [like we do for Windows now.] Our current research team is about 10 people, and they handle new threats via a hybrid approach of some manual work and some automated processing. We’re able to scale the problem down by using our own engine.
Derrick: You also have user forums where samples are being submitted too, if I’m correct?
Marcin: Exactly. These forums are very valuable to us. This is where the “good stuff” is; the “gold” if that’s what you want to call it. These are new samples that most of the honeypots out there have not even seen.
Derrick: Looking at the trends in malware today, what do you feel will be the biggest threat in 2013? What should users be on the lookout for?
Marcin: Rootkits and Bootkits; anything with a *kit in it! Just today, I tweeted out about a new Windows 8 bootkit that is already proof-of-concept. Anything that starts before Windows loads, and has to do with driver-level changes; these are all scaling in severity where criminals are getting very good at what they do.
And the other ones are those still common today, like ransomware. These are the ones that infect your machine, place all your files into a .zip file, and then try to get you to purchase the unlocking password by providing a credit card number. This is ransomware at its finest, and they’re making good money from people. There will likely be a lot more evolution in this aspect of malware. It’s a money business for them now.
Derrick: Malwarebytes Anti-Malware has had a similar interface for the last few years. Can we expect any major changes to the product in the near future?
Marcin: We are actively developing version 2.0 in both interface and engine, so yes, something is in the pipeline for next year. That’s about all I’m going to say for now.
Derrick: Your company markets to a lot of different segments. Where do you feel the most demand is coming from these days?
Marcin: I feel it’s really balanced. We started in the consumer market, and that’s how we gained our popularity. People were fixing their computers at home, then went to work, and once the IT guy found out about it – it evolved via word of mouth, honestly. Corporate and small business in particular is definitely getting bigger for us, especially with the launch of the Enterprise edition we just released.
A lot of businesses are starting to understand that layered security is definitely the next evolution in protection. Having multiple scanning engines from different companies, where each company can be accountable for some aspect of protection, is starting to become key to many organizations. Universities and other schools are also buying into Anti-Malware at a fairly good rate.
Derrick: Does Malwarebytes have any intentions of becoming a rounded AV solution like NOD32 or Norton 360? What are some of the longer term plans for the software?
Marcin: It’s an option most definitely, but we want to stick to what we’re good at. I don’t want to create an AV software, and also have an anti-malware product, and end up becoming just as ineffective as some other bloated solutions on the market. People may then steer clear from installing Anti-Malware alongside an anti-virus solution because they think one program handles it all. This is not the approach we want to push.
We’re able to do everything with a 10MB installer, where other programs have a tough time in shipping with less than 100MB. It goes back to our grassroots feeling and our belief in the community at large.
Derrick: Your company analyzes more samples of malware than one can fathom. What exactly are the “worst of the worst” doing on systems today?
Marcin: That’s a good question. Back in 2005-2006, you had infections that were very simple to catch. Same MD5, same filename even – I believe one was even called nail.exe. You looked for the filename, you checked its version information, matched it to definitions, and you were done. Nowadays, you and I can go to a malicious website and get infected and end up with different variants of the same basic malware. Different MD5s, different file sizes – completely different malware.
You can see how this becomes a large problem for our security researchers. We’ve had to evolve into using heuristics and install-pattern behavior to detect modern malware. It’s becoming very challenging to detect much of what is out there.
Derrick: Do you feel that signature-based detection is going to be a thing of the past some day?
Marcin: It’s already gone. Our approach is a hybrid one with signatures and heuristics, where each supports the other. The days of pure definition-based removal are long gone. Amateurs are using that now to make quick and easy malware. But if you look at all the sophisticated malware out there – the rootkits, for example – the nature of polymorphism is the scariest aspect of all this. And most major malware is using it these days.
For example, you may get hit with malware from a website claiming to offer keygens. You attempt to remove part of the infection, but the malware itself is so advanced that it will regenerate on its own and replace the missing files with fresh ones. You can’t even nuke these infections piece by piece anymore.
Derrick: Where do you see as being the largest source of infections today?
Marcin: It’s tough to answer, but social media is definitely the hottest one on the rise. The reason being is that with social media, it’s so easy to play off emotion to easily spread infections. You can post a link on a friend’s page saying “Hey, here is a photo of you – click to check it out” and by human nature, we are more likely to click on it as opposed to if we received it in an email.
Even if 10% of your friends click on it, and those friends of friends then see, it can spread very very quickly. That’s definitely on the rise and honestly a genius idea for how to spread malware.
Exploits from Java and Adobe are ones that are sticking around, too. The bad guys keep finding holes in this combination of software. The final big source of infection is still from people knowingly going to torrent and P2P websites, infecting themselves very easily.
Derrick: We now know that the upcoming Windows 8 is going to offer a bevy of security improvements such as Secure Boot. Is this going to pose an issue to Malwarebytes in the short or longer term in regards to functionality/capability?
Marcin: I don’t think it will pose too much of an issue honestly. We will work with Microsoft to ensure our product is as effective as possible. But what I fear is that with all of this deep-rooted security, we may actually see fewer, albeit bigger-impact breaches that will be harder to clean up and cause potentially more damage than what we see today. But it’s hard to predict that far out.
Derrick: There are a few top competitors out there alongside Malwarebytes Anti-Malware. What do you feel is the single feature that sets your product apart form the rest?
Marcin: There’s a lot of cool things that we offer in our software product (scheduled scanning, small updates, dual-protection modules, etc.) But the best way we differentiate ourselves is if you have an infection that Anti-Malware cannot remove, you can come to our forums and we will help you remove it for free. This is even if you are not a paying customer, and is just one of the perks that comes with our product.
Something also has to be said for our detection rates and removal success rates. This is how we grew to where we are; we are very comprehensive in our detection & removal approach.
But most important is our community approach to solving malware problems. When I had issues with an infection years ago, I will always remember how I came to a security forum to get help, and people had open arms. So I have a strong belief in this method of helping others.
Derrick: Knowing that Technibble is a place where IT professionals come for advice, is there anything you want to share with everyone as a final word?
Marcin: I think the best way to close out this discussion would be to open up the floor, so to say, to all the Technibble followers. What is it that you want to see in Malwarebytes Anti-Malware? What suggestions do you have for us? We’re very interested in hearing from the community that uses our product religiously – so please leave your suggestions in the comments area below!
Note: The original interview with Marcin took place on October 23, 2012. This interview transcript was edited for length considerations and editorial clarity.
Session expired
Please log in again. The login page will open in a new tab. After logging in you can close it and return to this page.

Malwarebytes Antimalware is a great product.
Whenever a PC comes in with an infection I make a clone of the disk (just in case) and then my first step is always MBAM in safe mode with networking – 99% of the time MBAM will install and update.
Then all that’s left is cleaning up and repairs.
A few times rootkits have thwarted the first pass however and so my suggestion is a rootkit scan and removal on reboot (from safe mode back to safe mode?
Maybe I’m just being lazy.
I was reading up on malware removal standard procedures for Experts at experts-exchange.com and they state that MBAM should not be run in safe mode (unless you have to because of the infection). They state that the design of MBAM requires you run in normal mode to allow it to hook into the filesystem at the deepest levels to be able to remove malware. Here is the quote from “younghv” (http://www.experts-exchange.com/Software/Internet_Email/Anti_Spyware/A_6650-Malware-Fighting-Best-Practices.html),
“If your computer will boot to “Normal Mode”, then in all cases that is how you should attempt to make the repair.
(The following comments are courtesy of rpggamergirl):
During a Safe Mode boot, most malware processes are not running and Malwarebytes’ heuristic detection can’t detect them.
Malware processes must be active while doing the scan so scanning in Safe Mode is not going to be as effective.
Malwarebytes’ Direct Disk Access (DDA) is not running so the detection of rootkits and other stealth hidden nasties in this mode is not optimized.
While malware processes are not active in Safe Mode, most rootkits are – so MBAM is disadvantaged and will miss detecting them.
Windows File Protection is not on in Safe Mode in Windows 2000/XP/2003 Server so any patched system files e.g. explorer.exe, winlogon.exe, userinit.exe that are deleted by the scanner will not be replaced.”
I had been using Safe Mode as well and wasn’t aware of this.
A portable version that does not need installed for technician usage would be nice.
I second the idea of a portable tech version. Also, the manner which a technician can resell the product needs to be reviewed. I’ve been trying to become a reseller for a year, and gave up recently. Otherwise, I love this product.
First of all, thanks for doing this article. Absolutely awesome!
I would also like to add that I too would LOVE to see a truly portable version of this software.
Unfortunately, like Mo, I too have been trying to become a reseller, and have recently given up due to convoluted and confusing policies and practices. I still recommend the free version to my clients, but would love to be able to offer the full version.
After many attempts to apply as a reseller and no response, I eventually received an answer. Evidently, if you do not plan on reselling a large quantity, they will simply refer you to their primary distributor: DSolution. They offer a reseller discount, but sometimes the reseller price is barely less than the Amazon price. However, they do offer the corporate version as well, which I have yet to see offered elsewhere.
Here is the response:
“Thank you for signing up to be a reseller with Malwarebytes Corporation. We have been quite busy committing resources into research and development of our products to continually improve them. Unfortunately we are not able to take on as many partners as we would like. I am putting you in touch with our preferred distributor DSolution.”
1) IT / Portable version
2) IT Pricing
3) MSP Model for 1-100 seats. Management console like enterprise with wholesale per seat licensing.
4) Simpler partner process for resellers
With several bringing up the process for partner/resellers, how bad is it?
I agree that the process for becoming a reseller needs improvement. I’ve signed up 3-4 times over the past year and haven’t heard any communication back. An IT version would be nice as well.
Thanks for the article, and a special thanks to Marcin Kleczynski for such a fine product and his community approach.
I like the idea of a portable version.
What I would really like to see, is a version that will run in Linux to scan a Windows machine. My general practice to clean infected PCs, is to boot into Linux on the machine, remove all temp files, and look for obvious malware stuff to delete. The problem I see with running Malwarebytes in Windows, is that the malware is live.
I usually boot to a live Windows CD to do my initial scan… this takes all the live malware out of the equation
It’s interesting, as I read these comments that people are describing their methods of cleaning which were similar to mine, until I read some articles on experts-exchange.com about the proper way to remove malware *these* days. I also posted a similar comment, above about scanning in safe mode which is no longer recommended. In this case, you wonder about an offline scanner, using Linux that would scan and clean and you also mention clearing temp files (which I used to do) before scanning. Both methods are apparently not a good idea, per younghv and rpgamergirl, (both long-time, highly respected experts there). Regarding any offline scanning, they say that you can’t do that effectively, and you might cause more problems, because if the hard drive isn’t active, with the registry in memory, the scanner can’t connect an “infected” file with the registry hooks it’s linked to and therefore you end up with double work, or reinfections, etc. Also, Deleting temp folders and files and turning off system restore is a bad idea right away because a) temp folders may actually contain ransomed user files you need to restore and b) having an infected restore point is more helpful and quicker if the repair goes bad than having no restore point, or having to clone a drive again.
Here’s the article which sums up their recommended procedures: http://www.experts-exchange.com/Software/Internet_Email/Anti_Spyware/A_6650-Malware-Fighting-Best-Practices.html
Just thought I’d share what I learned.
very interesting article
I would like to see a portable scanner, as many here have said. Almost all of the malware removal software I use is standalone or is offered in a portable version, with the exception of Malwarebytes’ Anti-Malware. Examples include SUPERAntiSpyware, Kaspersky Lab’s TDSSKiller, GMER, and ComboFix.
I am glad to hear that Malwarebytes is looking to expand into the Mac market, but while on the topic of Unix and Unix-like systems, I would second the argument for a Linux-based tool. Another solution may be to, at the very least, make a Malwarebytes LiveCD/LiveDVD or LiveUSB for download, similar to what many antivirus companies offer, based on a flavor of Linux or BSD.
To Marcin, thank you for a very effective product. We see a lot of infected computers and count heavily on Malwarebytes. We too would like to see a portable verion of Malwarebytes. We would like to see a release that would allow us to customize which drives should be scanned, be able to bypass music and MS document files,and be able to change the priority. Please keep focused on what your company does best. We used a licensed product and would purchase a portable version.
Thank you RickNCN for that very valuable information. I will certainly adjust my methodology.