F1ComputerServices
New Member
- Reaction score
- 6
- Location
- Canada
Overview
I need to access a shared folder on a remote computer (Server2021) using VPN across WAN from a local computer Laptop-016I can connect to the remote ROUTER using VPN but cannot see or connect to the remote Server2021
I expected to see in the explorer of Laptop-016 all the resources and shares on its local LAN AND the resources and shares on the remote LAN – including Server2021.
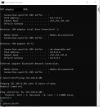
I can connect from Windows to the Remote VPN router. The Remote router shows I am connected. I check my IPCONFIG and it shows I am connected to the remote router.
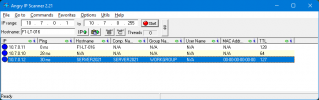
I do an IP Scan (angryIP) on both subnets from Laptop-016 and Laptop-016 appears
I am missing something! I think there has to be some more adjustment in the remote router to connect the Remote LAN to the VPN.
I have called TP-Link support – but they are going down the wrong rabbit hole.
Thank you for filling in the blanks in my knowledge here.
Rob
Server2021 Settings
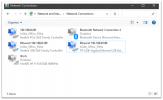
Remote Router confirmation
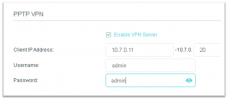
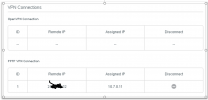
From Laptop-016;
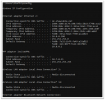
Proof of problem.
Scan of Remote IPs from local Laptop-016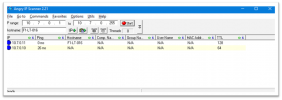
Scan of Remote IPs from Remote Server2021