HCHTech
Well-Known Member
- Reaction score
- 3,835
- Location
- Pittsburgh, PA - USA
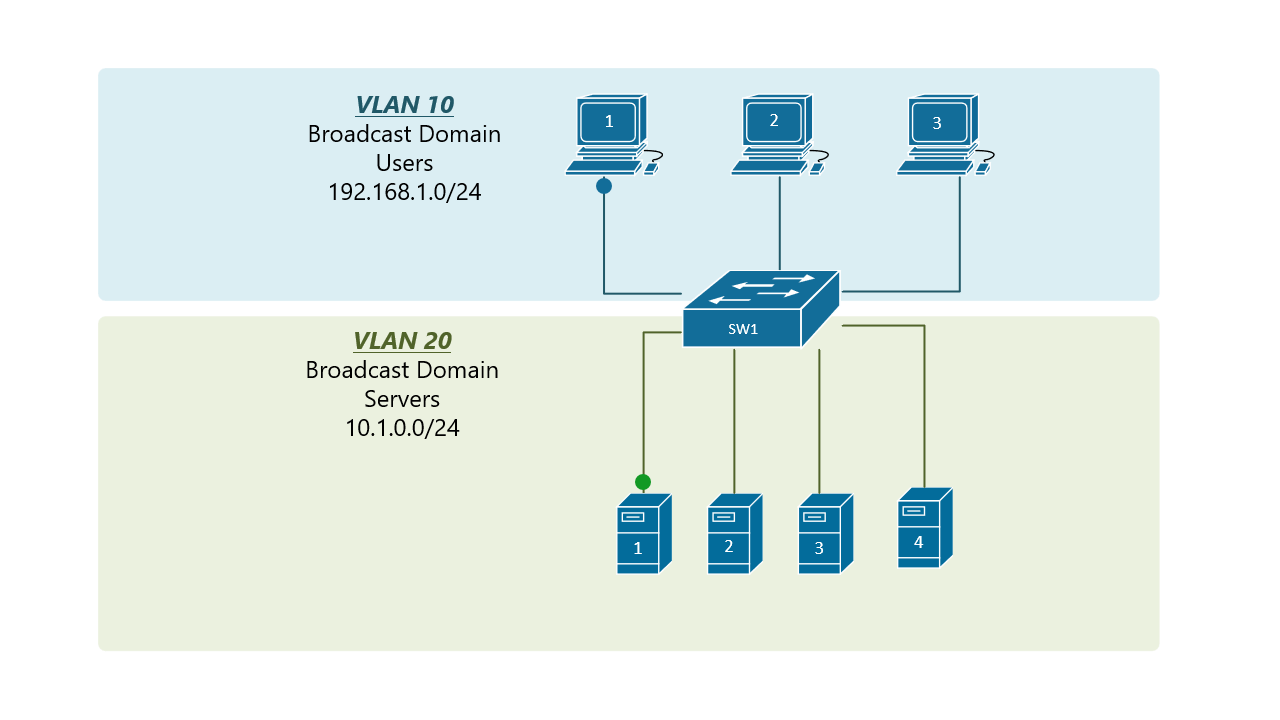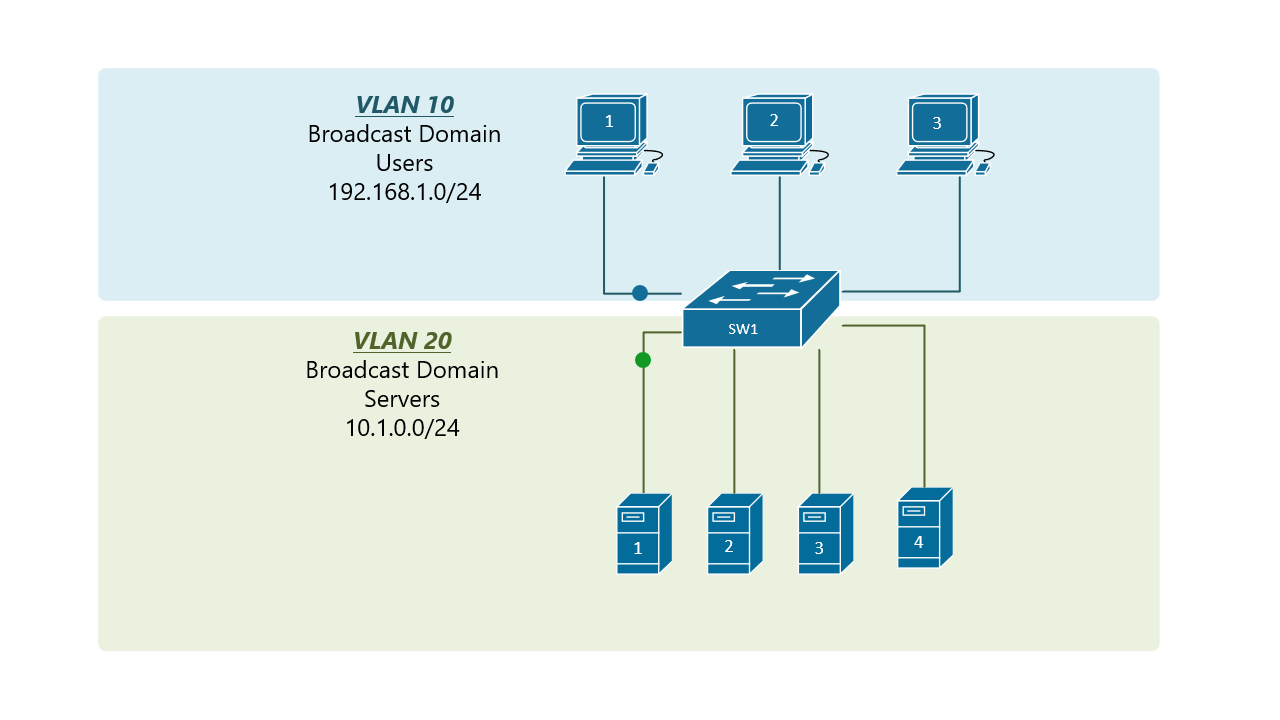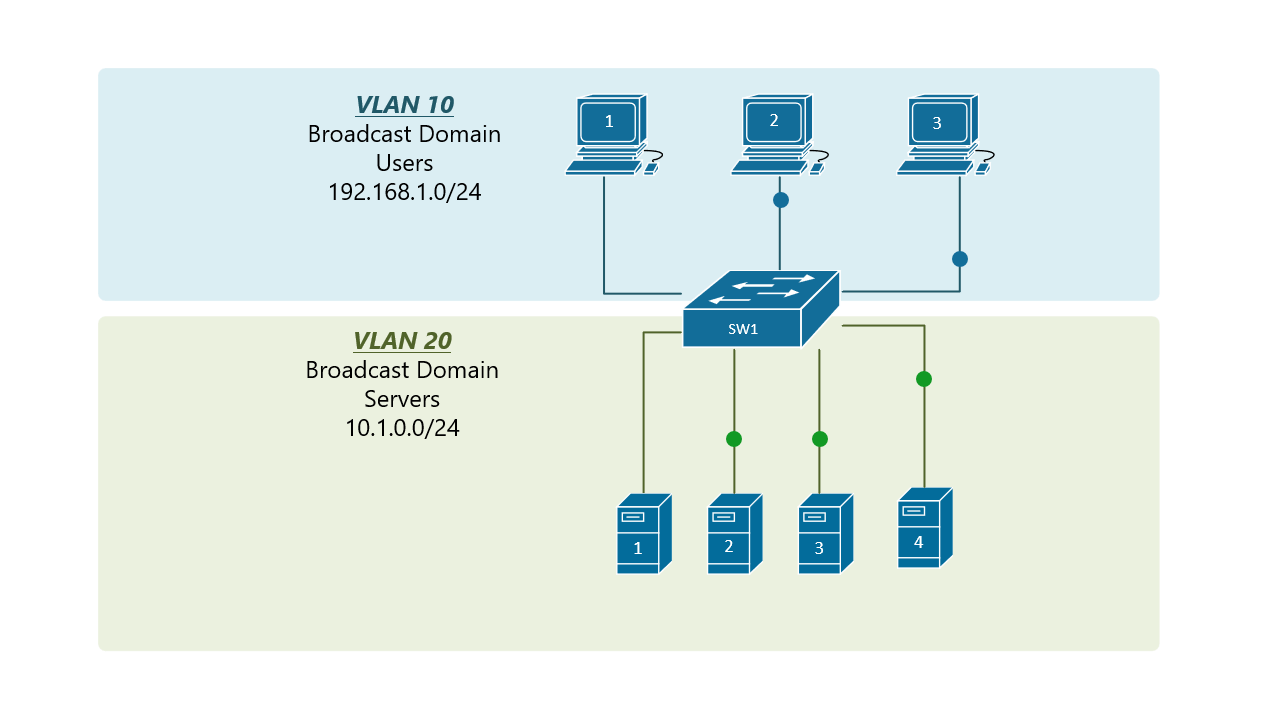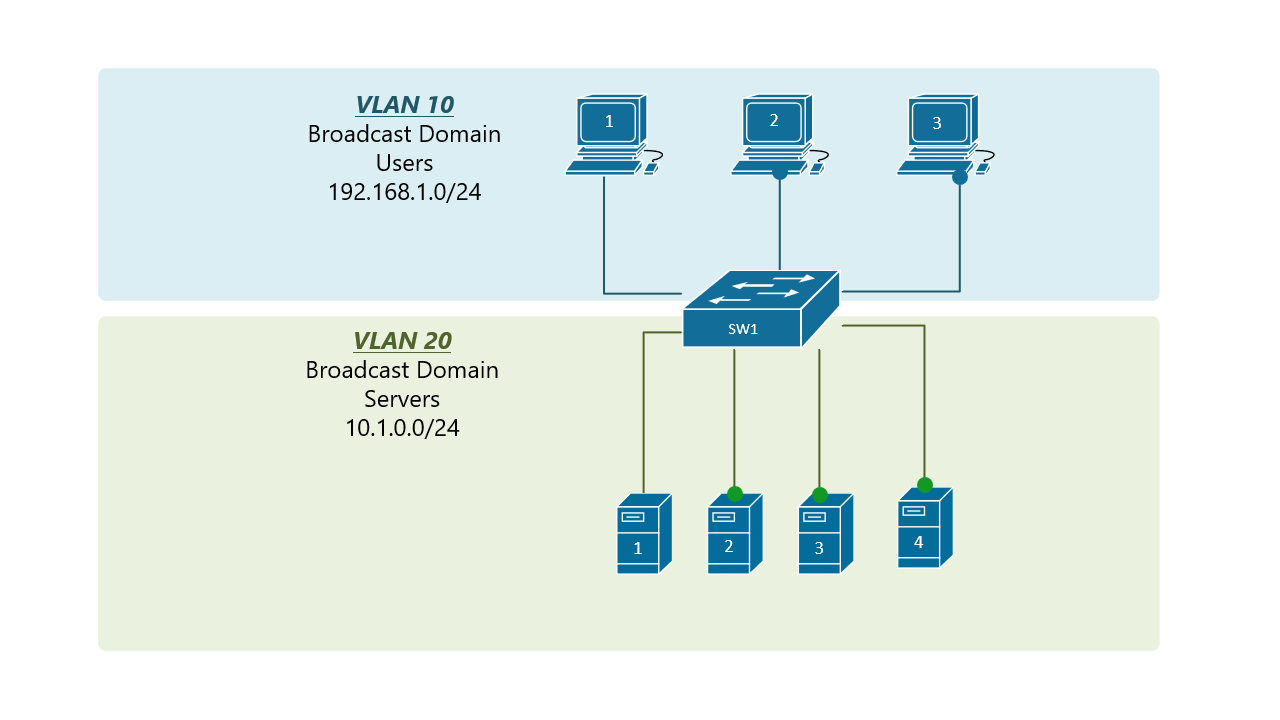
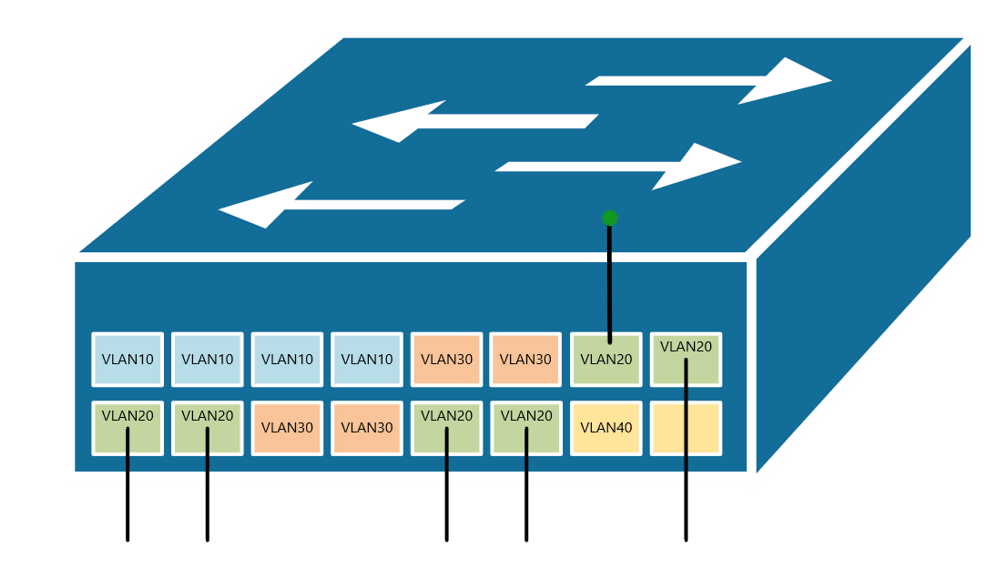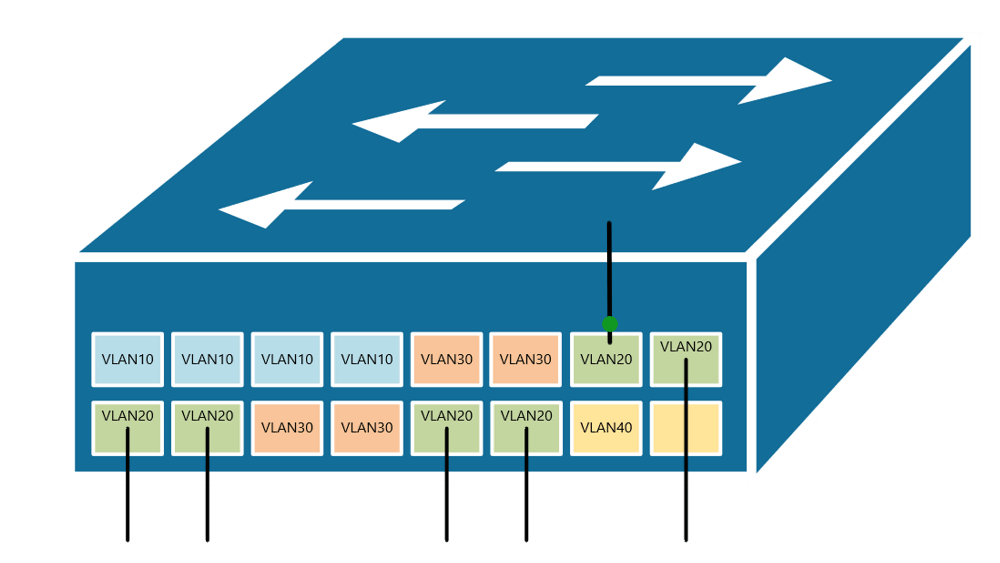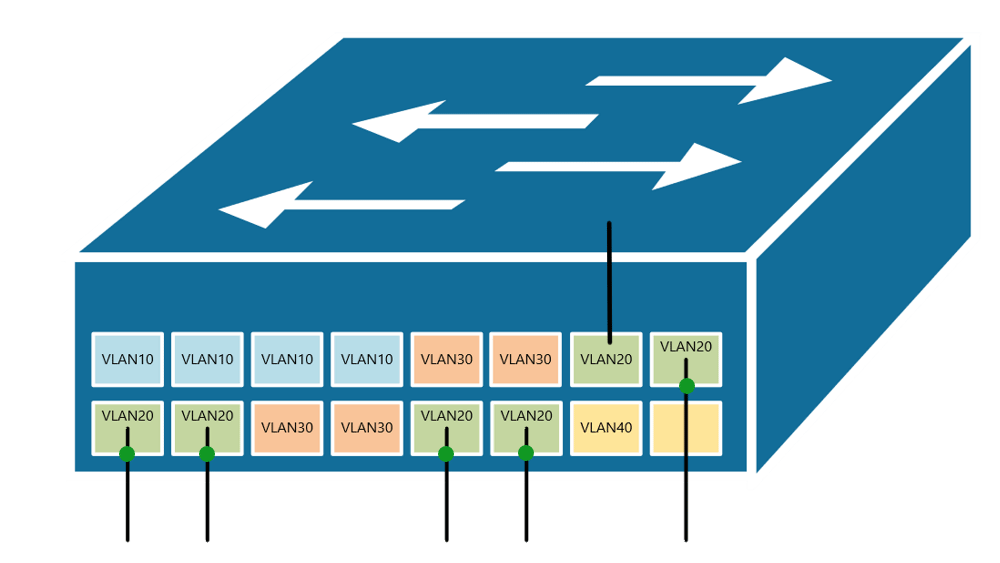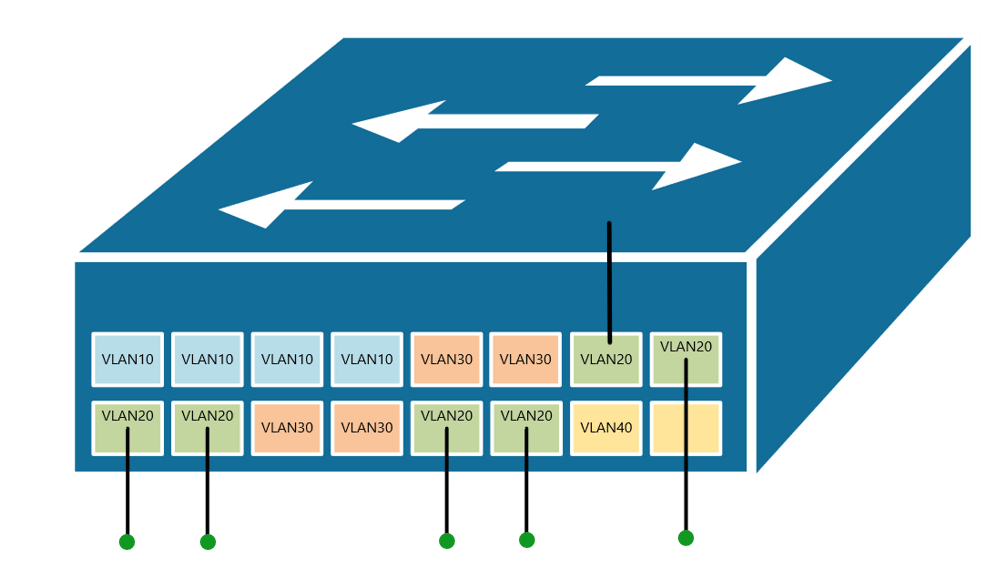
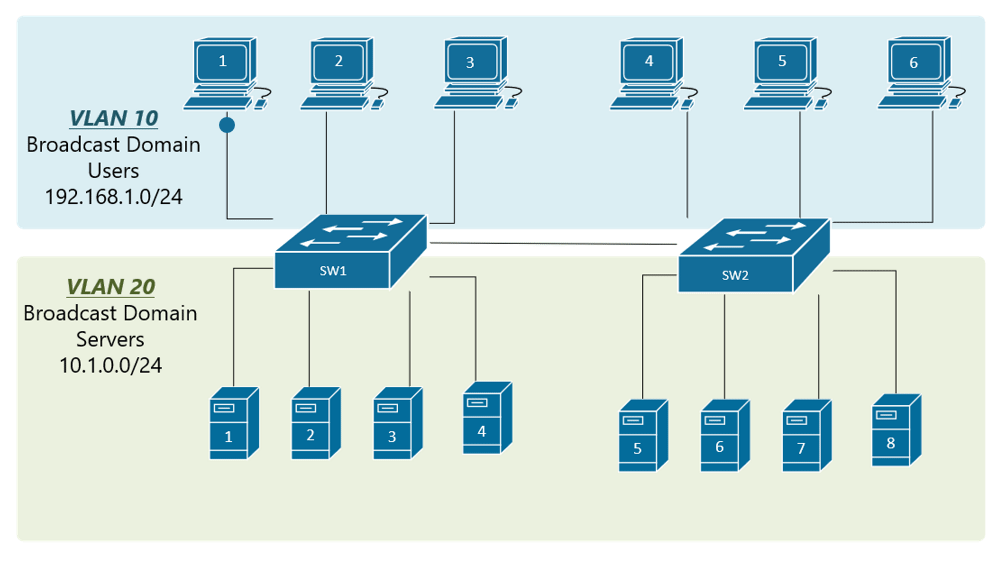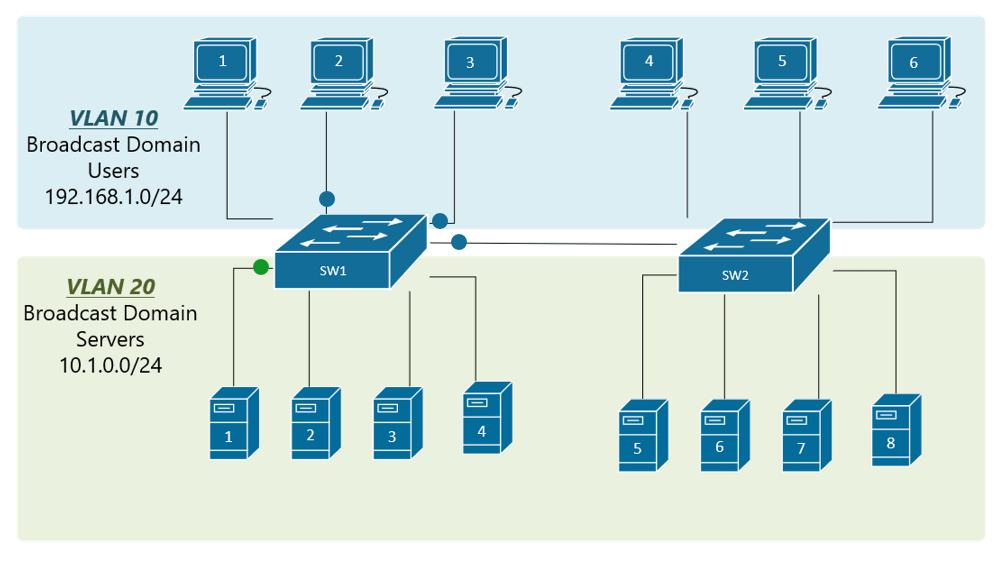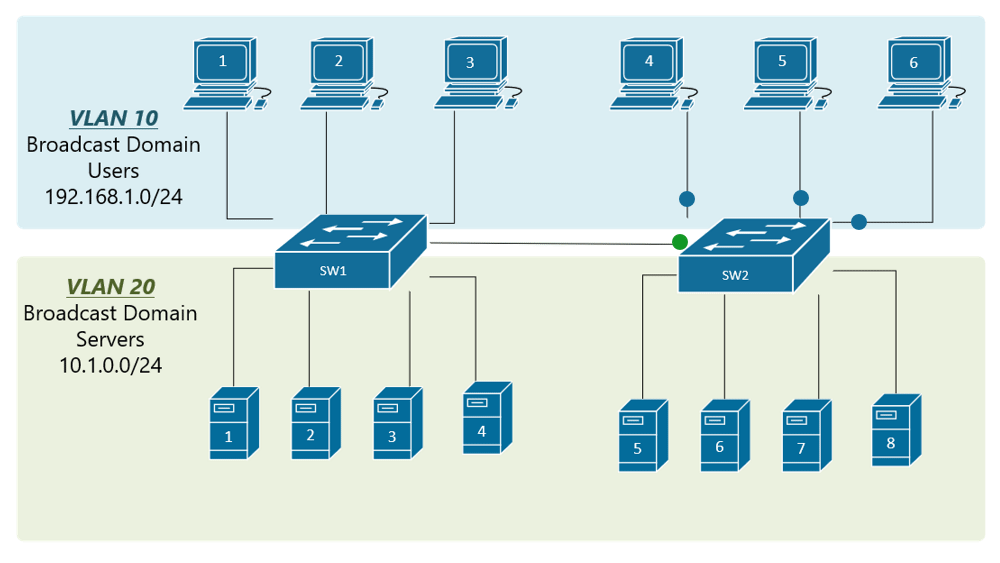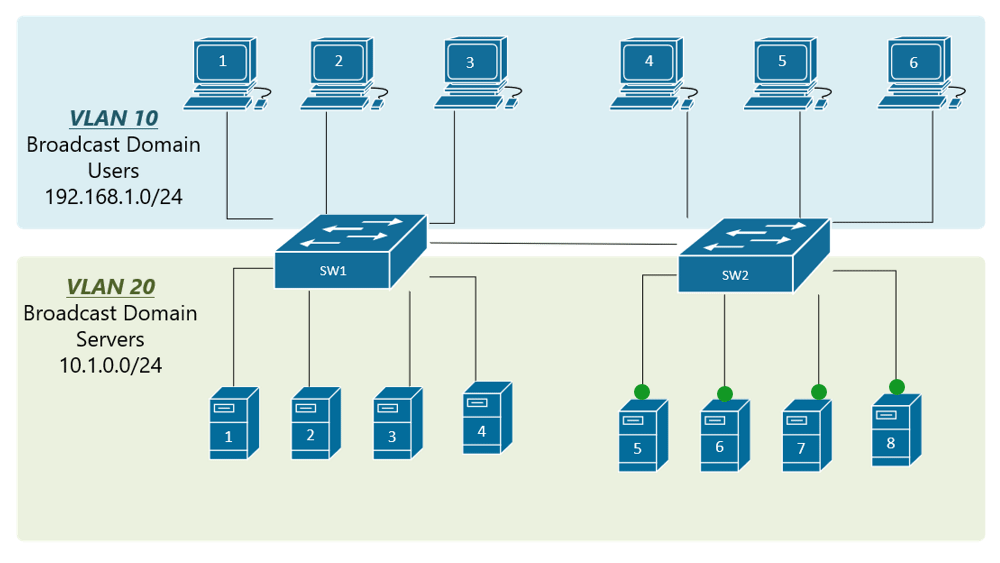
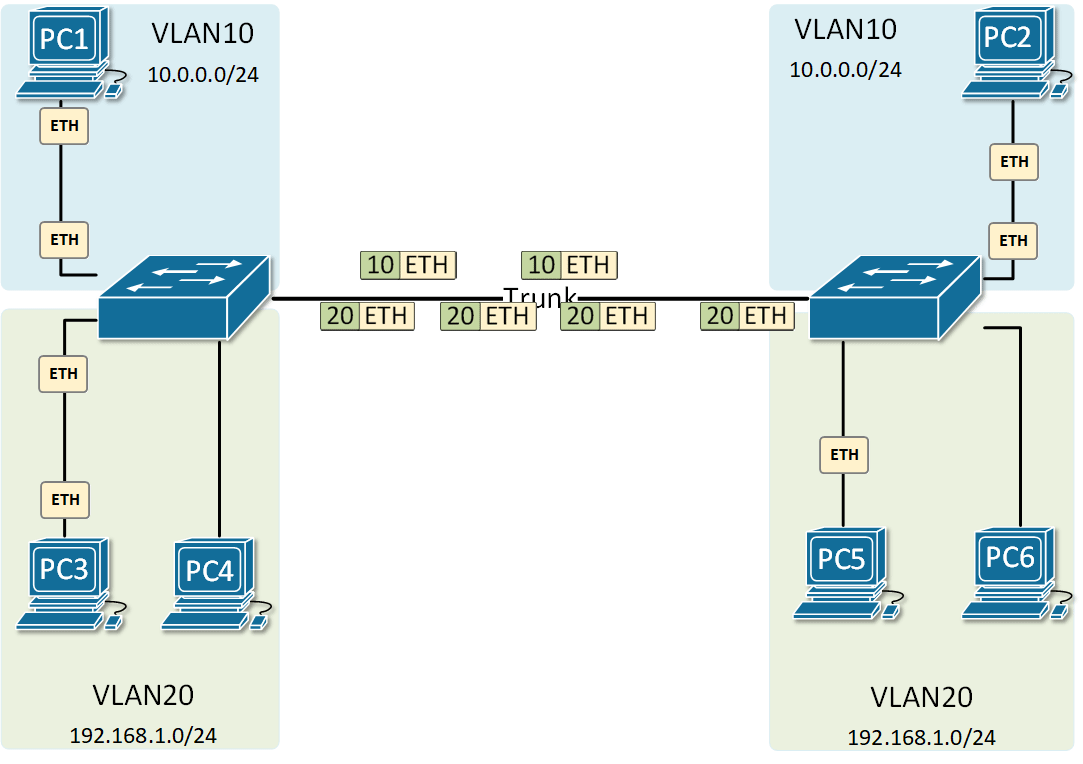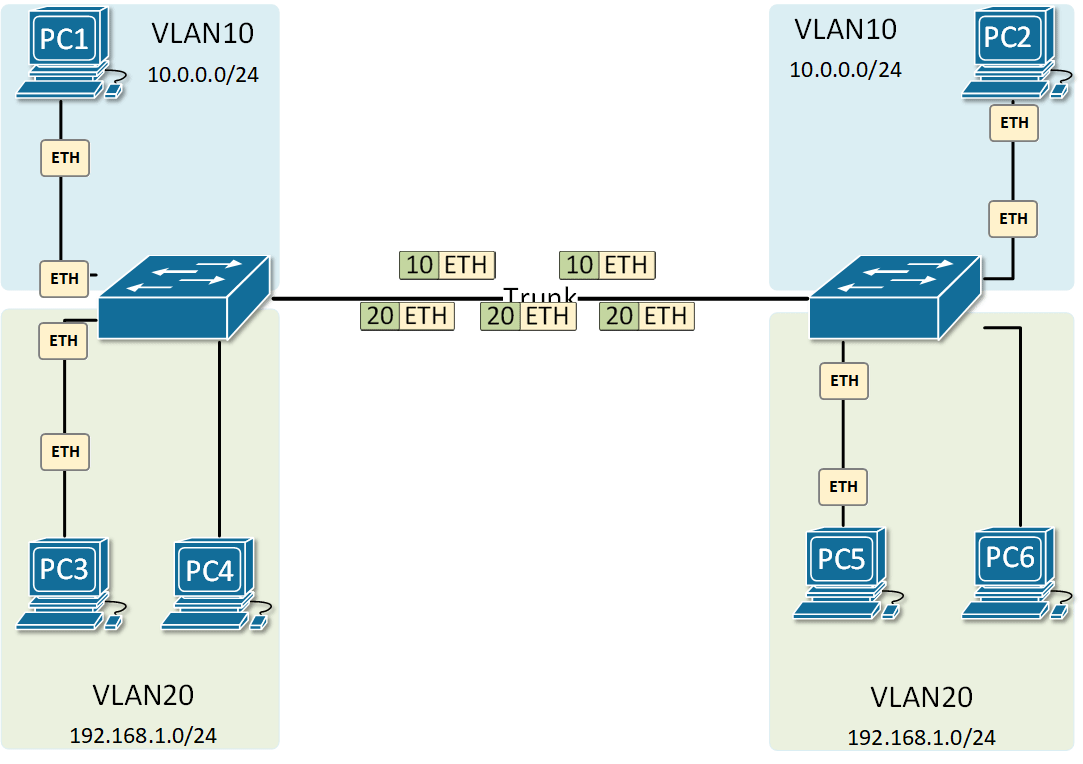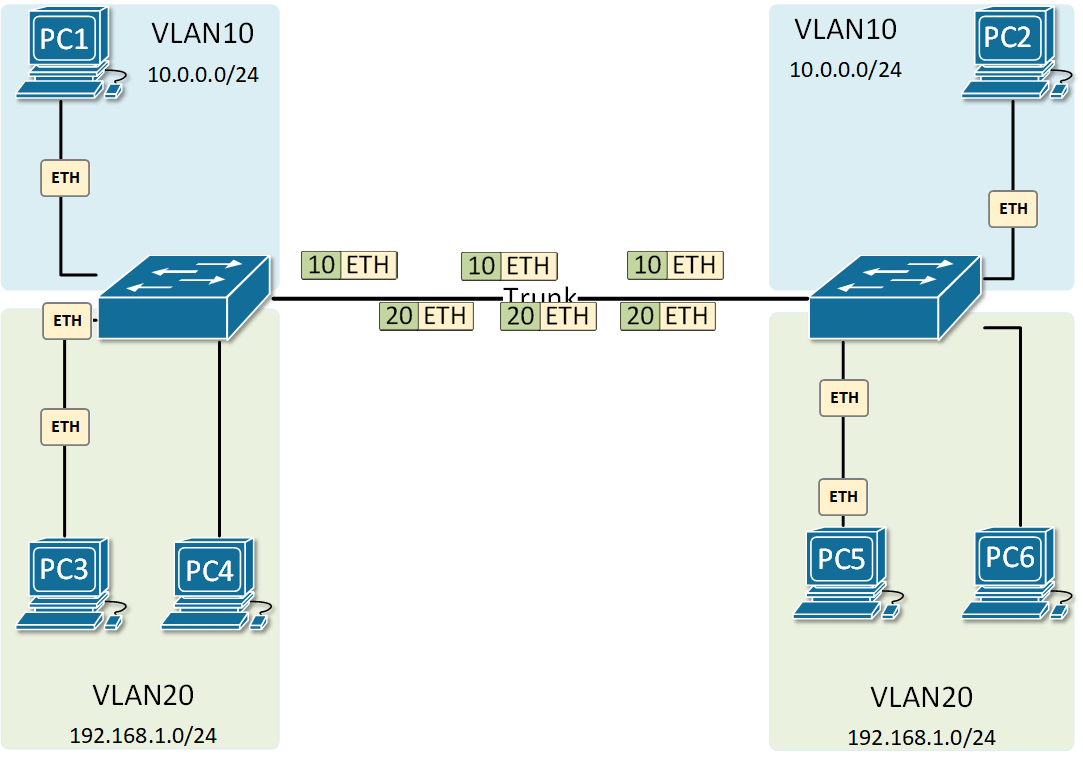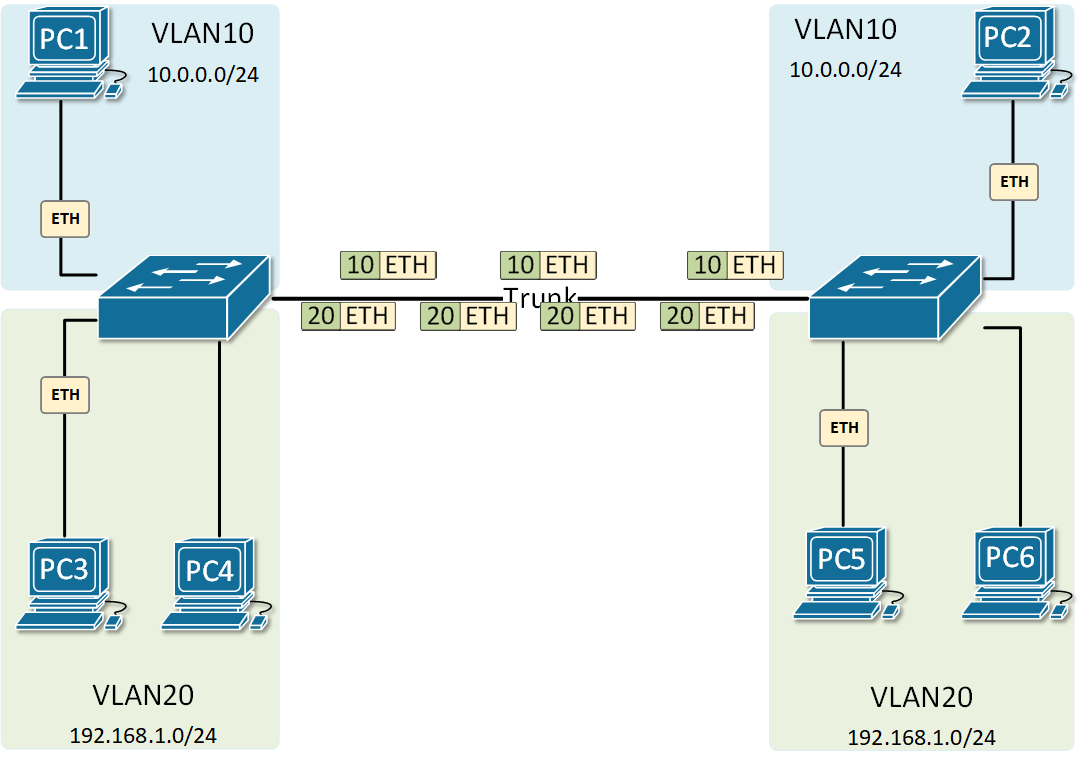
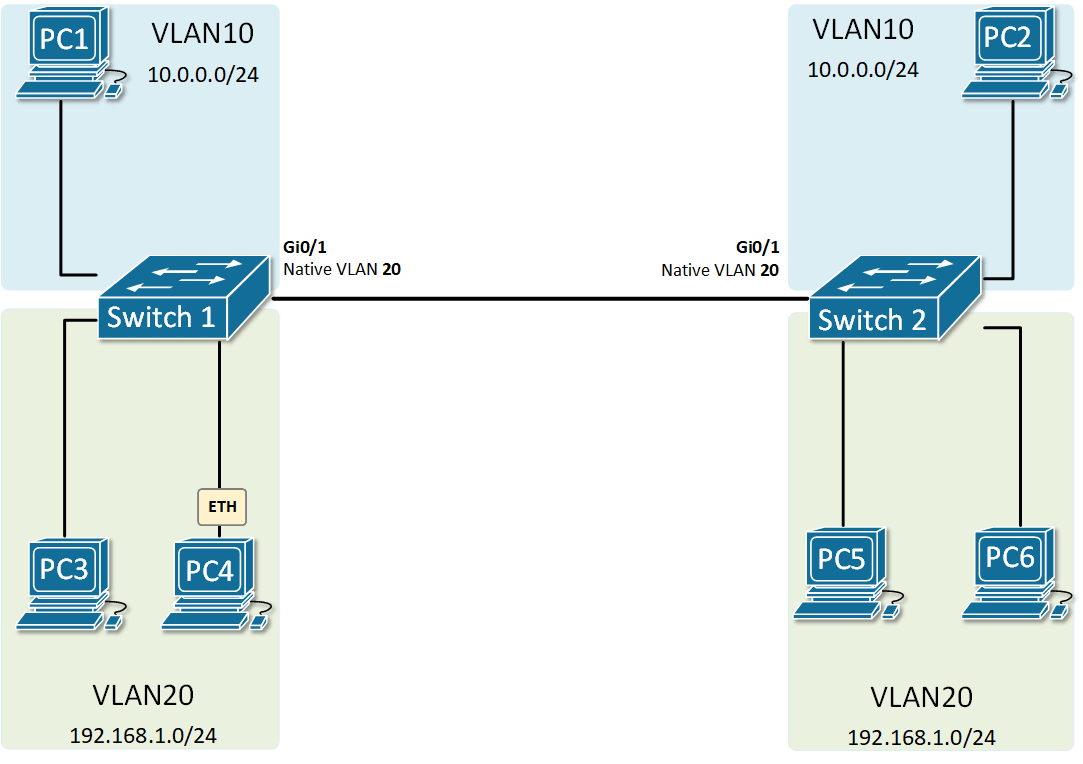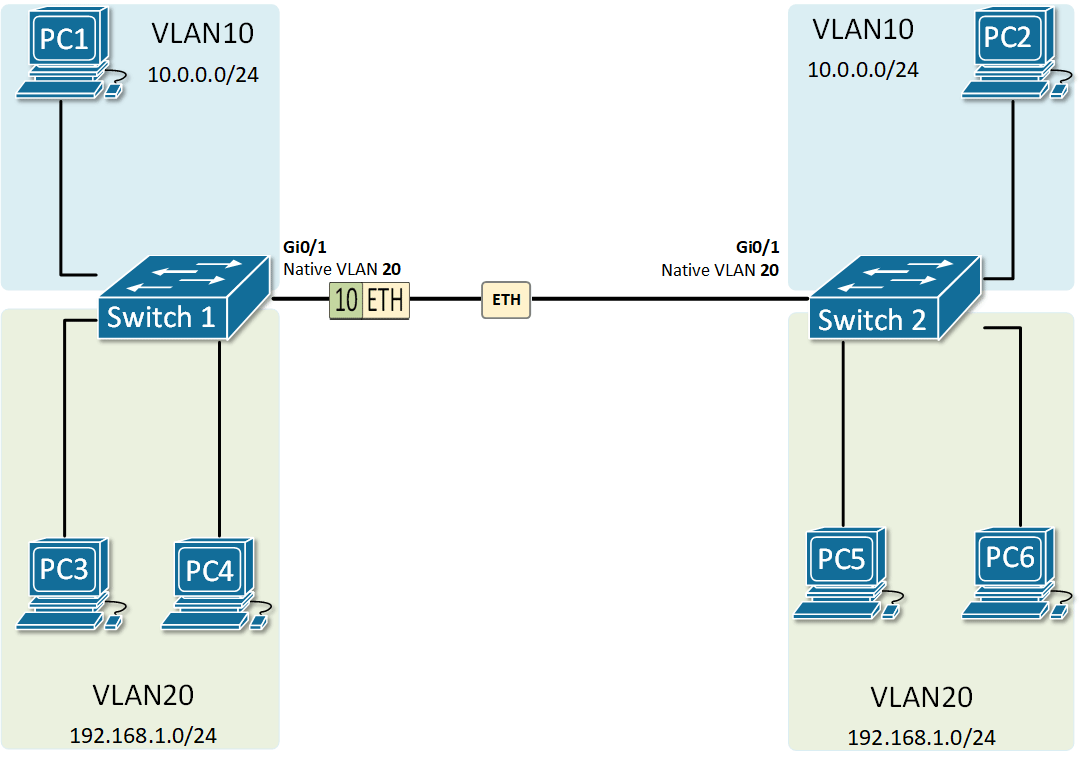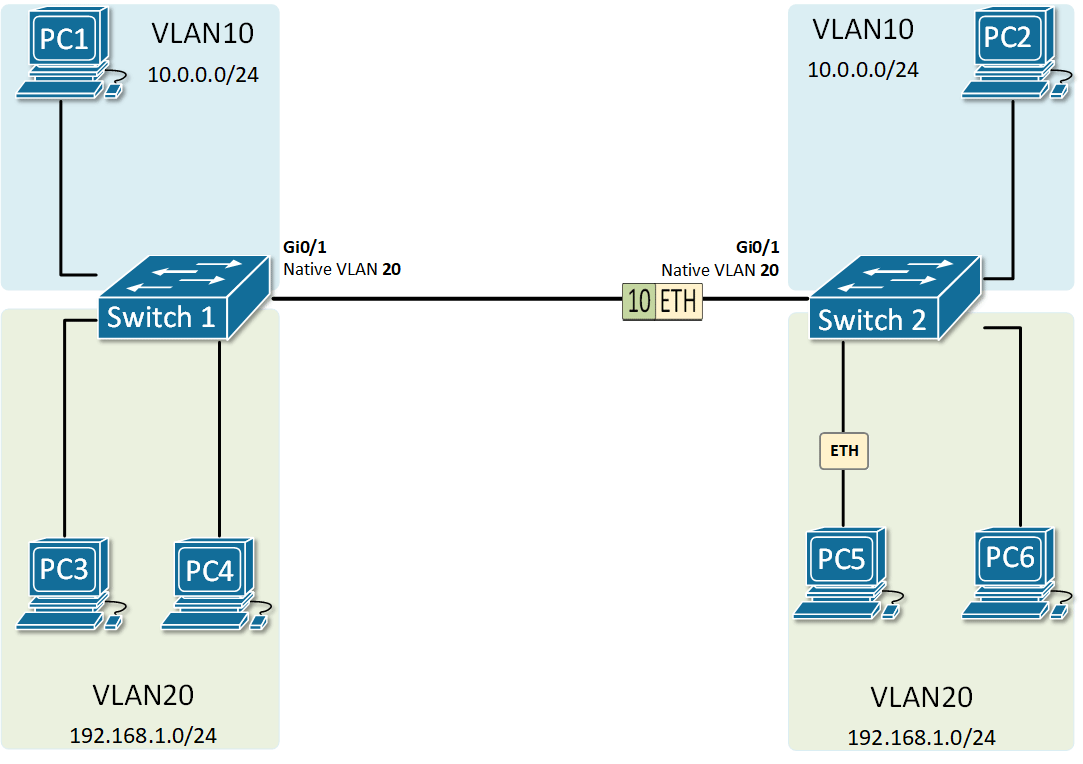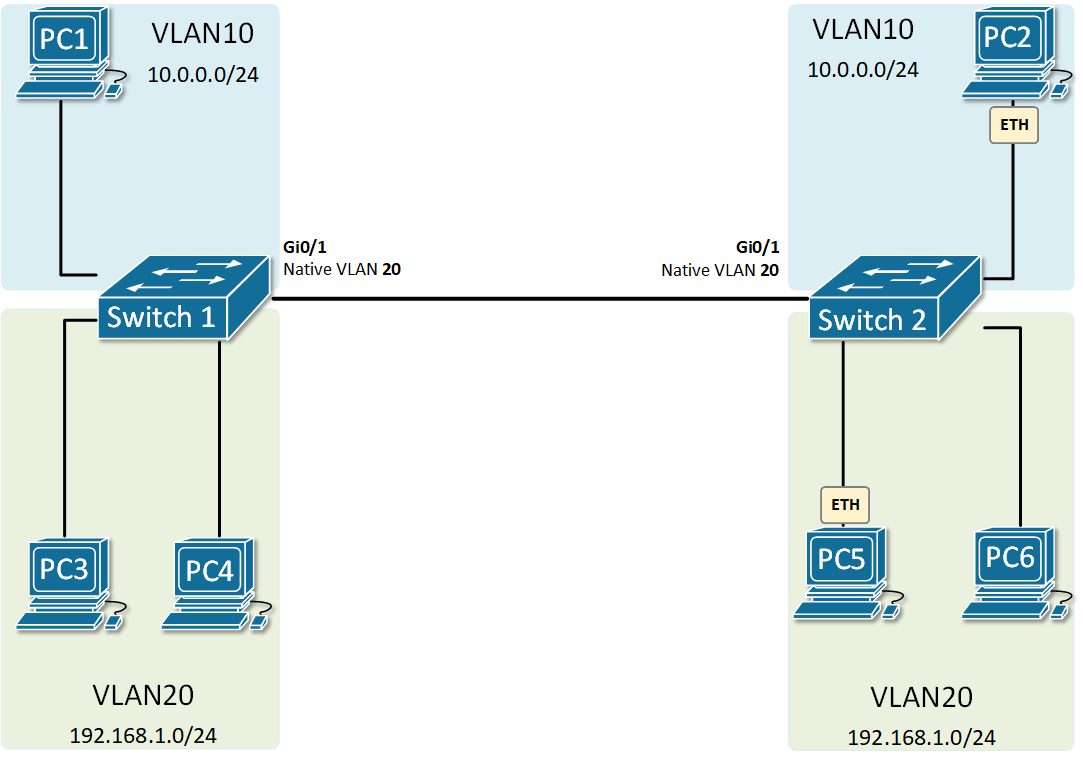
At the risk of asking a dumb question (never stopped me before!), I have a query about VLANs. Some background:
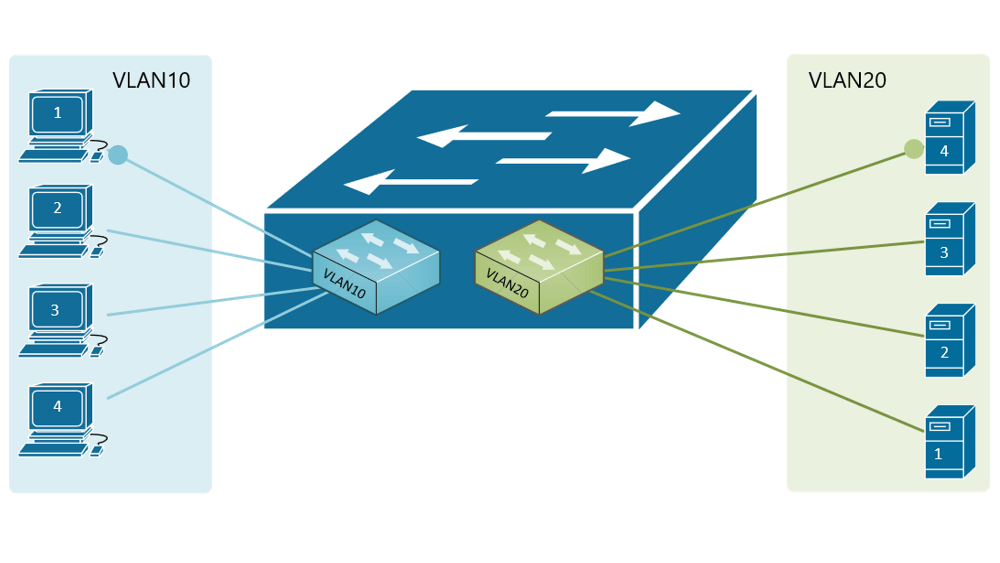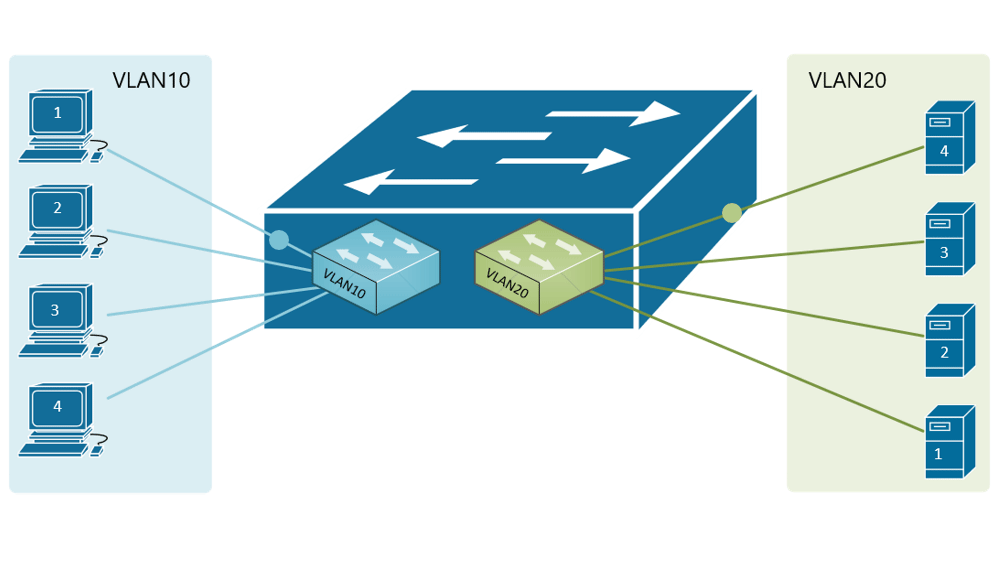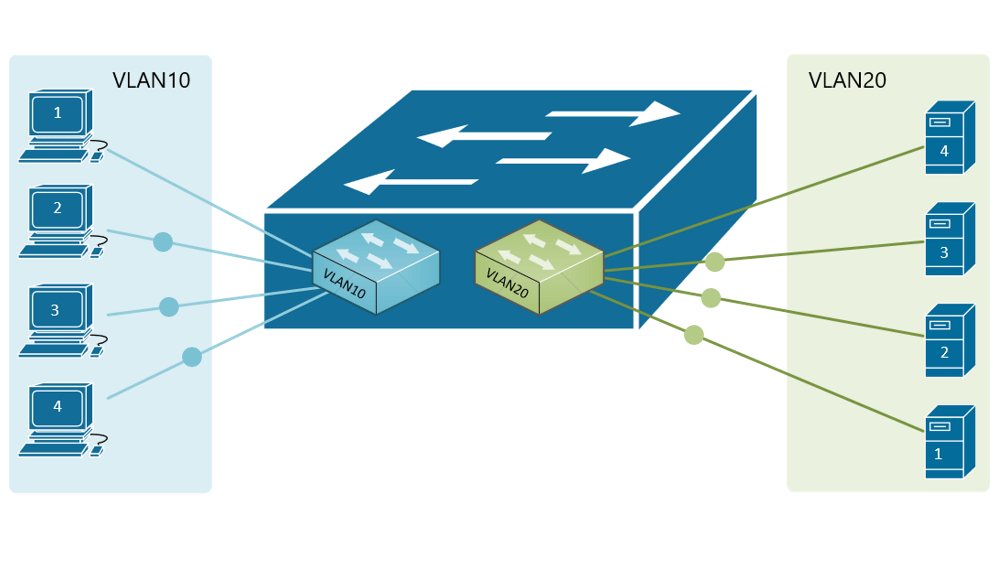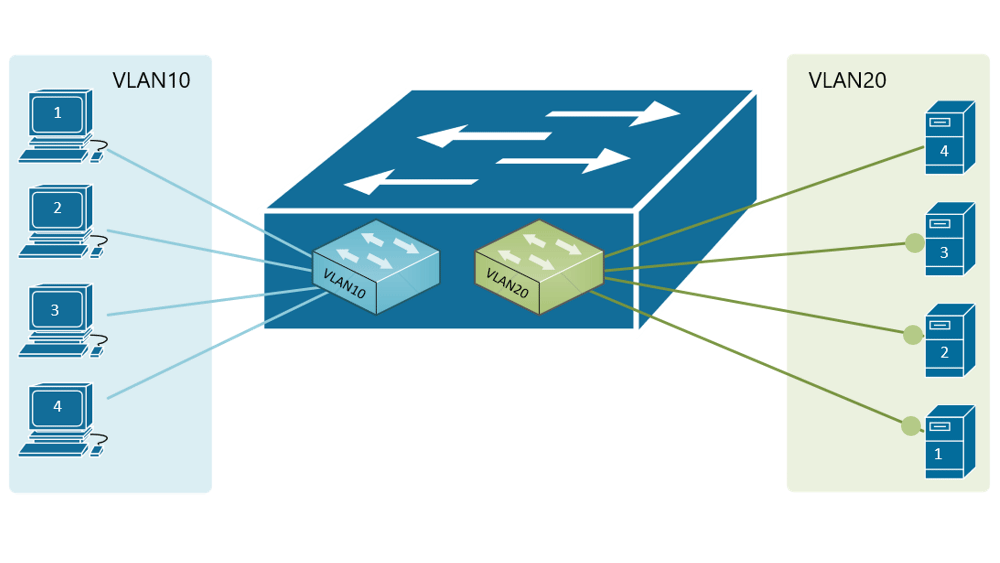
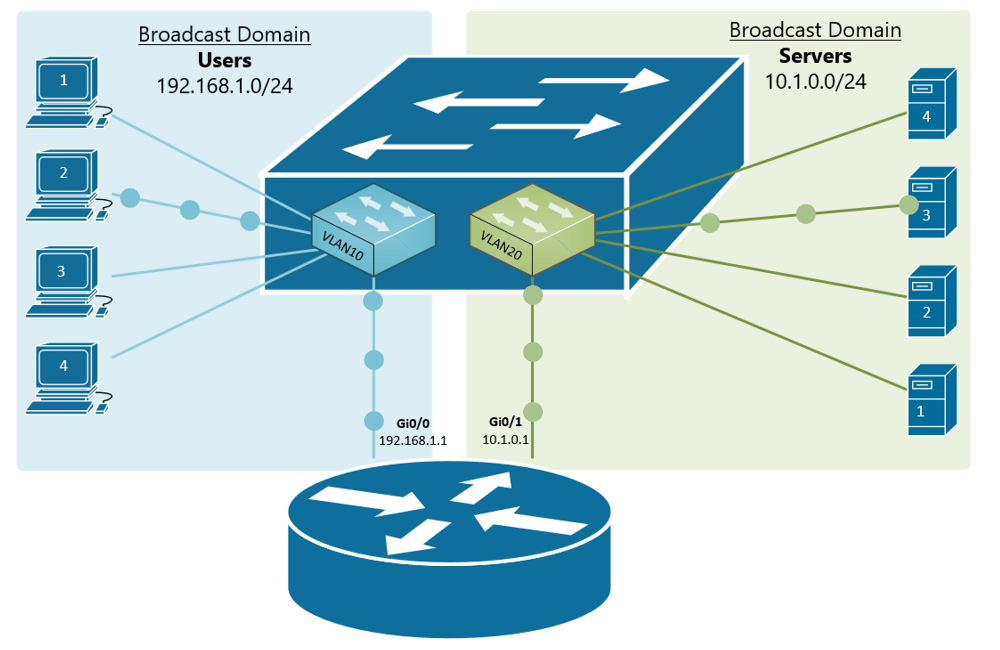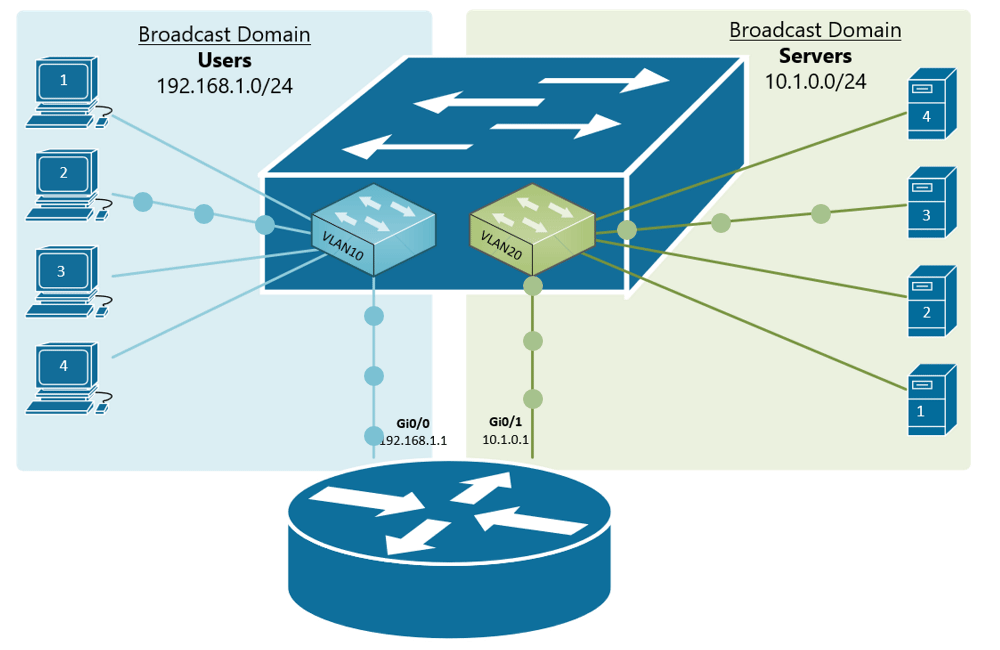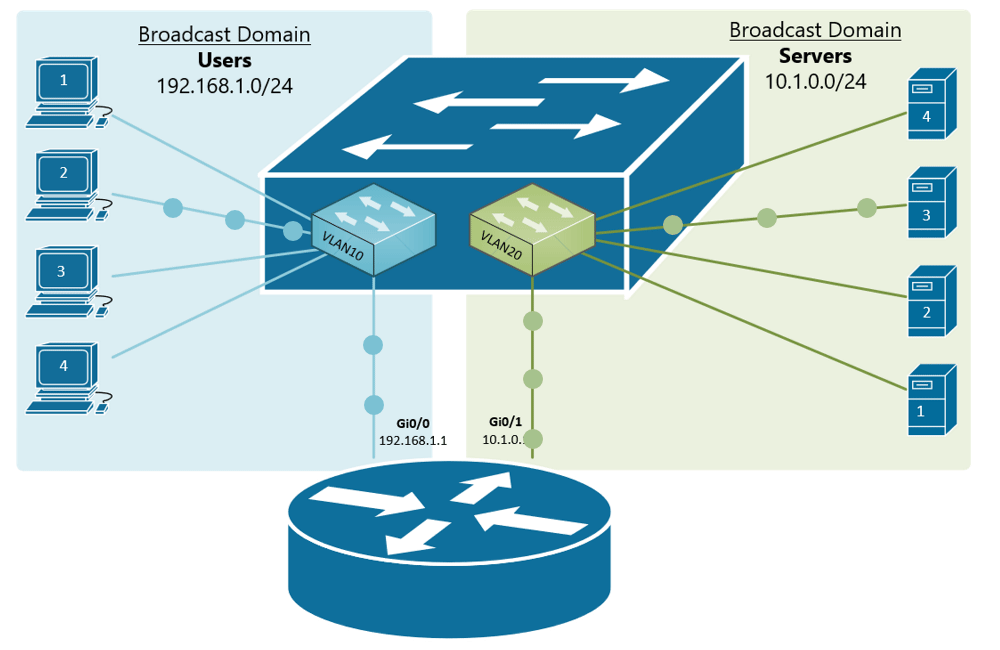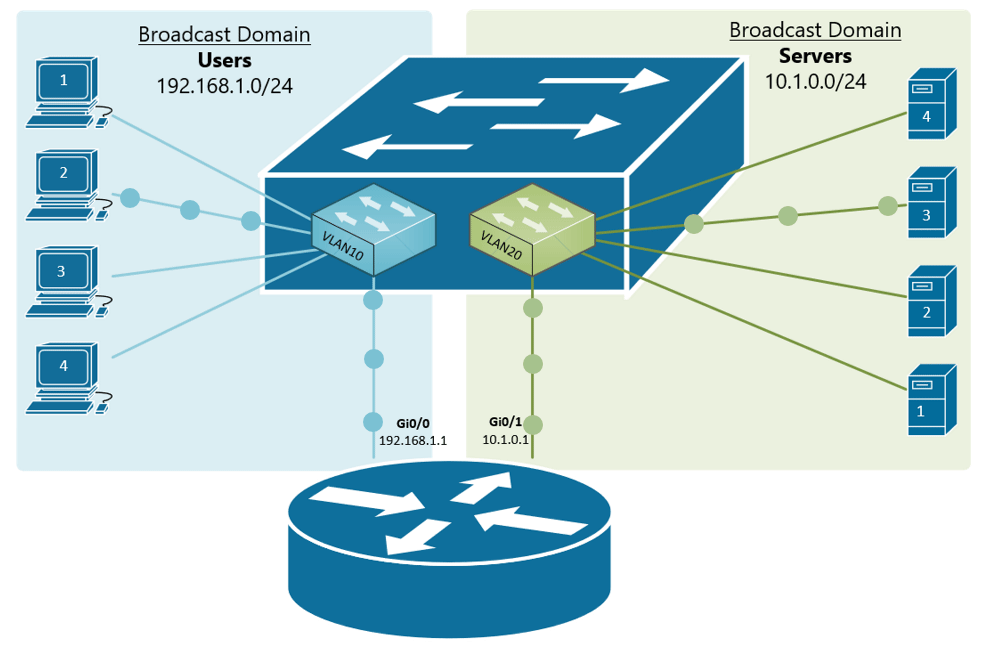
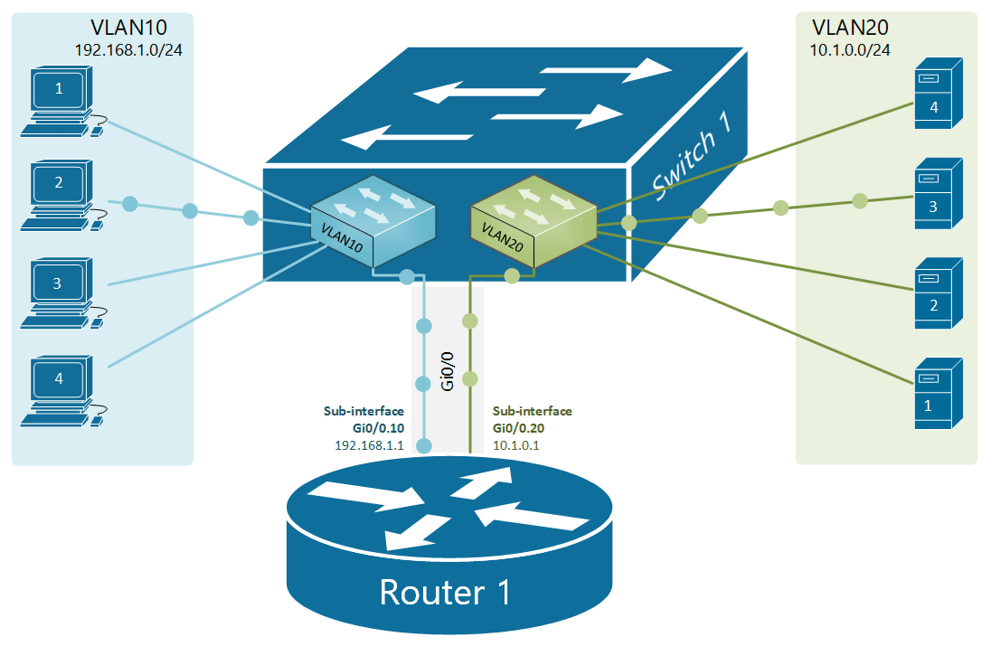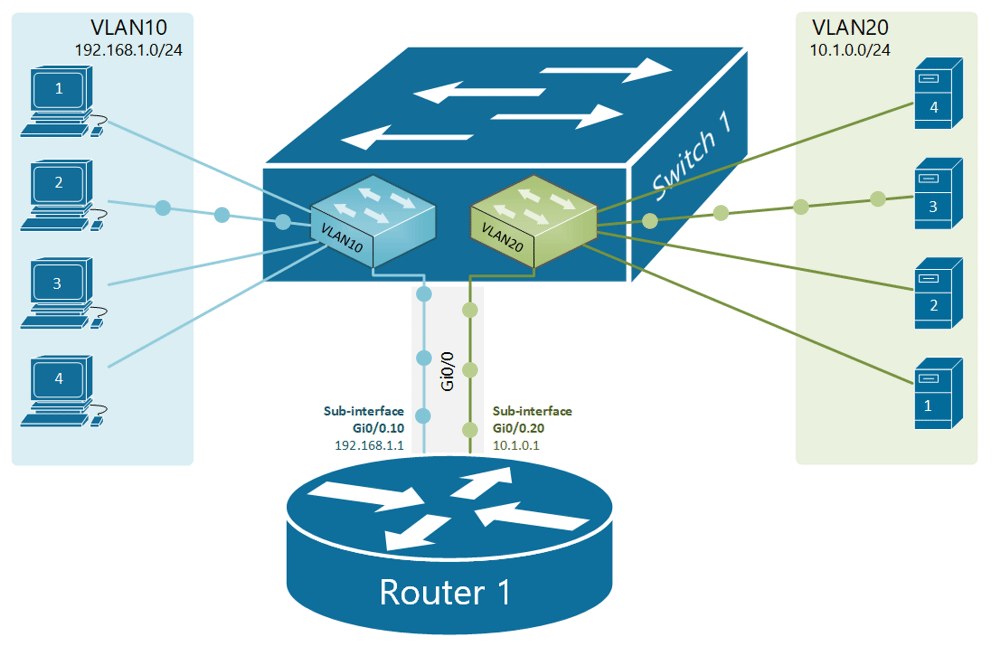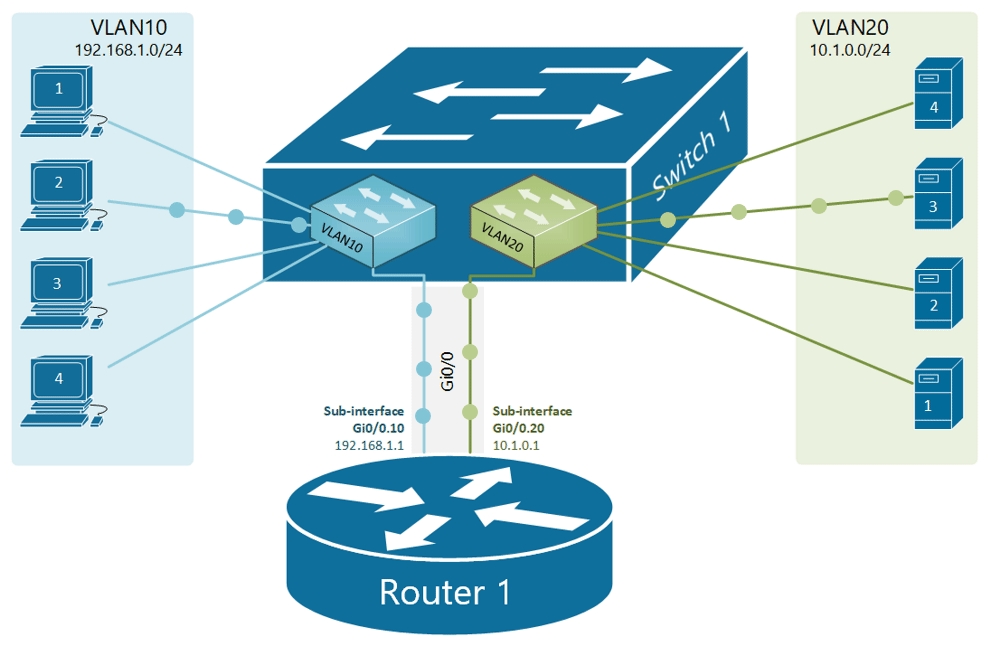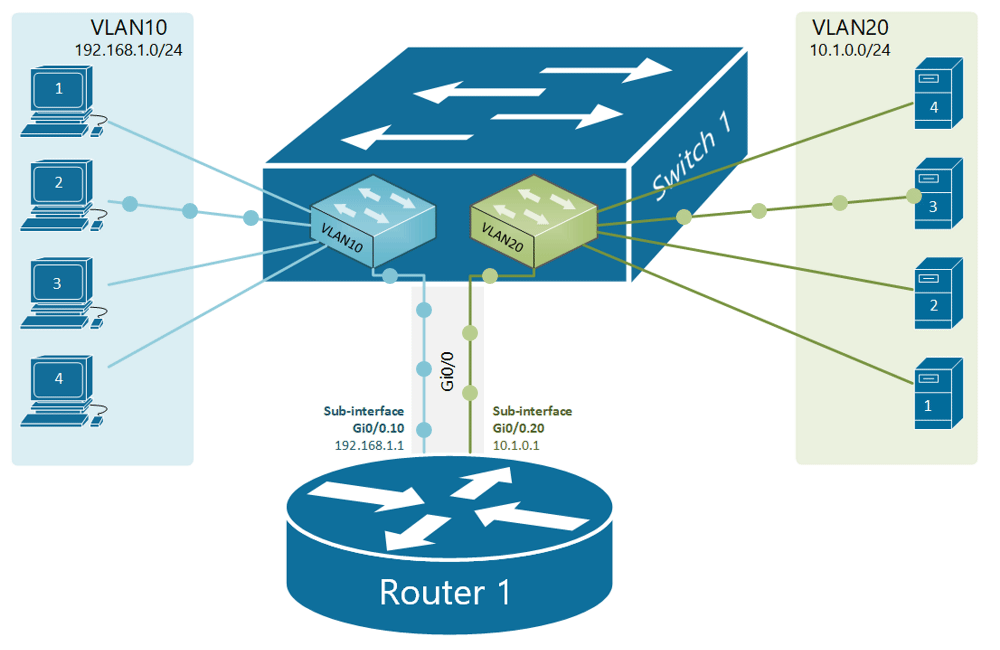
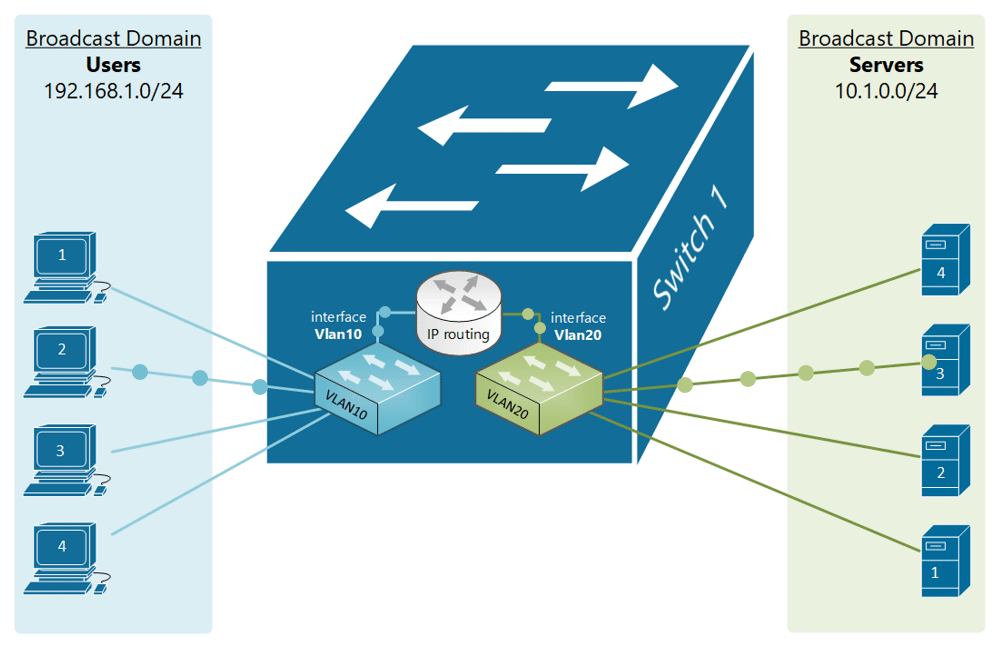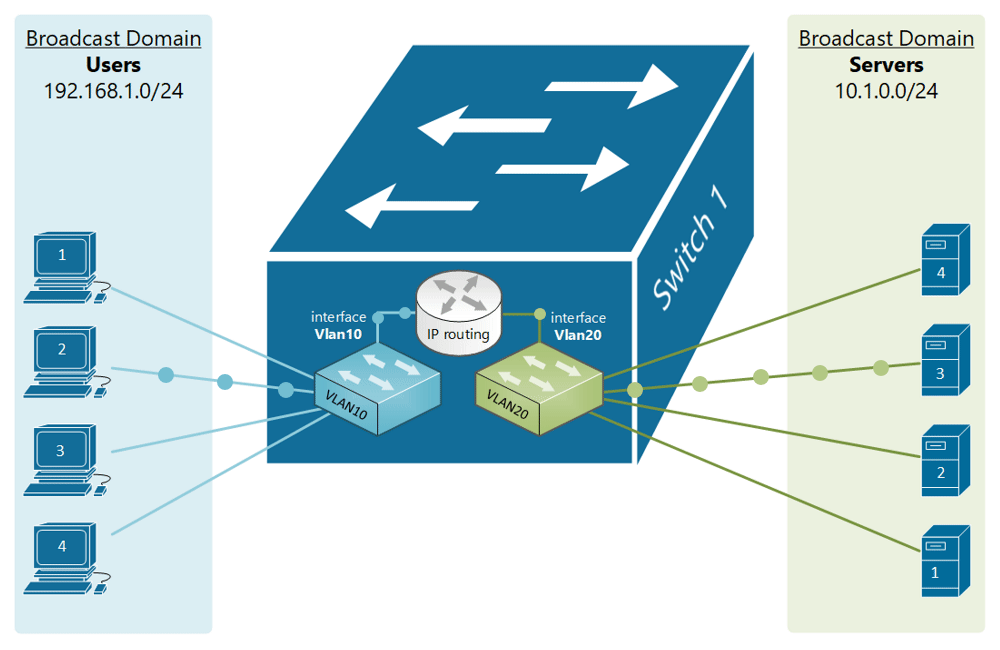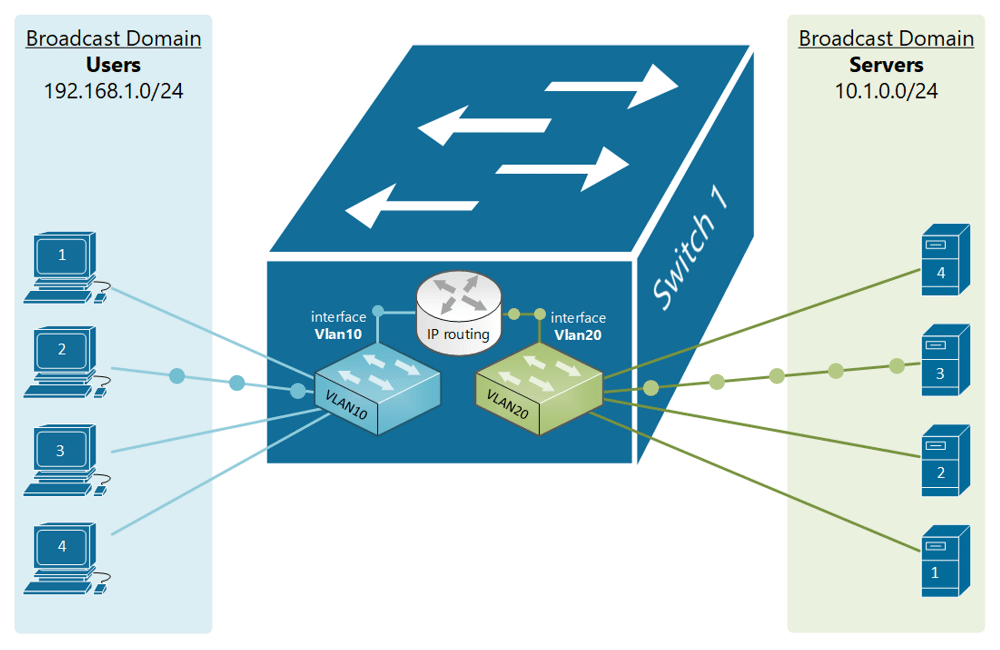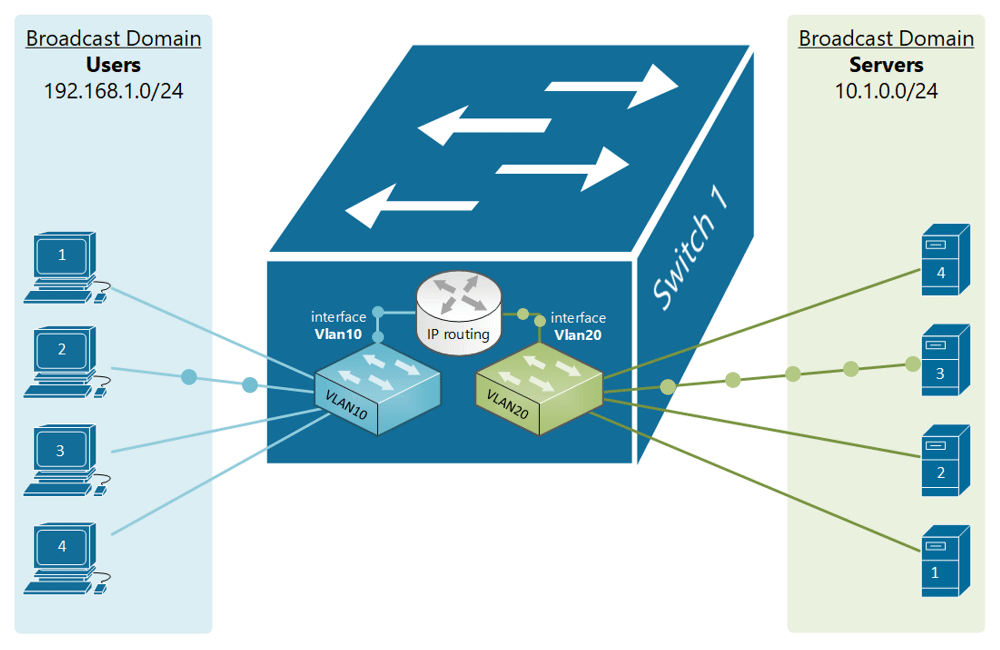
If, for example, a customer has a non-converged IP phone installation, you can physically separate the phones by setting up two LANs on the firewall, and have two separate switches - no need for a VLAN at all.
If the device (like phones or access points) can tag traffic, you can setup the VLAN without involving any programming of the switch. You configure the tag on the device(s) and configure the firewall to separate that traffic however you like.
My confusion surrounds why you would choose to program the switch and dedicate a port or range of ports to a specific VLAN. Is this more secure than relying on the firewall to separate the traffic based on the VLAN tag? Is it more efficient because it restricts the broadcast range on the switch? Once you program the switch, do VLAN tags even matter anymore - because traffic is physically separated (presuming you aren't doing anything with that traffic in the firewall other than giving it access to the internet)?
Thanks for indulging me!
- I'm in the SMB market, so don't ever work with multi-thousand dollar switches or equipment. My clients have a firewall at the edge and 1-3 switches
- Most of the time, the reason I set up VLANs is for guest wireless, IP Phones, or IOT devices
- I'm self-taught - so my knowledge is the sum-total of my field experience, my own reading, plus a few thousand calls to tech support over the years - haha. I never had a mentor and was never an apprentice.
If, for example, a customer has a non-converged IP phone installation, you can physically separate the phones by setting up two LANs on the firewall, and have two separate switches - no need for a VLAN at all.
If the device (like phones or access points) can tag traffic, you can setup the VLAN without involving any programming of the switch. You configure the tag on the device(s) and configure the firewall to separate that traffic however you like.
My confusion surrounds why you would choose to program the switch and dedicate a port or range of ports to a specific VLAN. Is this more secure than relying on the firewall to separate the traffic based on the VLAN tag? Is it more efficient because it restricts the broadcast range on the switch? Once you program the switch, do VLAN tags even matter anymore - because traffic is physically separated (presuming you aren't doing anything with that traffic in the firewall other than giving it access to the internet)?
Thanks for indulging me!