HCHTech
Well-Known Member
- Reaction score
- 3,835
- Location
- Pittsburgh, PA - USA
I'm reviewing a 'friendly takeover' client from another company in my area. I've run into something I've not seen before so at the risk of exposing my ignorance, thought I would post here.
Customer has a single static IP service with Comcast business. They have a standard business gateway device - 8 LAN ports & built-in dual-band wifi. They also have a Sonicwall connected to the gateway, and it is pulling the public IP directly - as if the gateway is in bridge mode (or comcast's pseudo-bridge mode). All of the computers and other company devices are inside the firewall None of this is unusual, except they also have a handful of wireless phone base stations, which are connected directly to the Comcast gateway and not running through the Sonicwall. This surprises me since anytime I've seen a firewall pull the public IP directly for a customer with Comcast business, the rest of the LAN ports on the comcast gateway are inactive.
In this customer's case, it appears one of the LAN ports is serving the public IP to the Sonicwall, while the rest of the LAN ports are giving DHCP addresses on the 10.1.10.0/24 network.
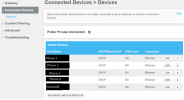
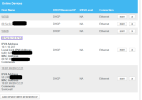
If I look at the Connected Devices pages of the Comcast gateway, I see this:
I don't understand how the Sonicwall can be on the DHCP list showing the public IP, while other devices on that same list are on the native 10.1.10.0/24 network.
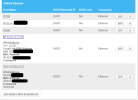
In the Comcast Network section, I see this (The public IP being pulled by the Sonicwall is the one starting with 50.248 ):
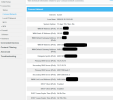
DHCP on the gateway is clearly active:
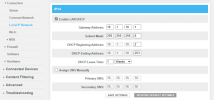
Does this imply there is some back-end routing going on somehow? There are no NAT rules or Static Routes in the Comcast gateway.
Everything is working, but I have no idea if this is an efficient setup or not. Usually the fewer things happening between the firewall and the internet the better, as far as I'm concerned. I'd rather bring the phone stuff inside of the firewall and manage them on their own VLAN, but this apparently unusual configuration is giving me pause.
Customer has a single static IP service with Comcast business. They have a standard business gateway device - 8 LAN ports & built-in dual-band wifi. They also have a Sonicwall connected to the gateway, and it is pulling the public IP directly - as if the gateway is in bridge mode (or comcast's pseudo-bridge mode). All of the computers and other company devices are inside the firewall None of this is unusual, except they also have a handful of wireless phone base stations, which are connected directly to the Comcast gateway and not running through the Sonicwall. This surprises me since anytime I've seen a firewall pull the public IP directly for a customer with Comcast business, the rest of the LAN ports on the comcast gateway are inactive.
In this customer's case, it appears one of the LAN ports is serving the public IP to the Sonicwall, while the rest of the LAN ports are giving DHCP addresses on the 10.1.10.0/24 network.
If I look at the Connected Devices pages of the Comcast gateway, I see this:

I don't understand how the Sonicwall can be on the DHCP list showing the public IP, while other devices on that same list are on the native 10.1.10.0/24 network.
In the Comcast Network section, I see this (The public IP being pulled by the Sonicwall is the one starting with 50.248 ):

DHCP on the gateway is clearly active:

Does this imply there is some back-end routing going on somehow? There are no NAT rules or Static Routes in the Comcast gateway.
Everything is working, but I have no idea if this is an efficient setup or not. Usually the fewer things happening between the firewall and the internet the better, as far as I'm concerned. I'd rather bring the phone stuff inside of the firewall and manage them on their own VLAN, but this apparently unusual configuration is giving me pause.