britechguy
Well-Known Member
- Reaction score
- 4,866
- Location
- Staunton, VA
I mentioned this in passing yesterday, and the folks at Namecheap stated they have no control over the issue, and that I needed to contact the developers of 2FAS, which I have done. There's now a ticket in on their GitHub site reporting this. In case this should occur for anyone else, for any token, the ticket is: Token for Namecheap being created with "Heap" as identifier
For reasons unknown, scanning the QR code from Namecheap for setting up MFA, resulted in a token branded "Heap" in 2FAS. This occurred twice. I deleted the initial token and tried again in hopes it was a "burp," but it wasn't. My guess is that "Heap" is the generic that gets used when the connection between the site and the database 2FAS uses to identify it somehow goes haywire and there's no match.
Here's a screenshot from 2FAS with the Heap entry at the bottom:
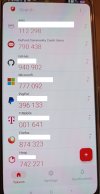
For reasons unknown, scanning the QR code from Namecheap for setting up MFA, resulted in a token branded "Heap" in 2FAS. This occurred twice. I deleted the initial token and tried again in hopes it was a "burp," but it wasn't. My guess is that "Heap" is the generic that gets used when the connection between the site and the database 2FAS uses to identify it somehow goes haywire and there's no match.
Here's a screenshot from 2FAS with the Heap entry at the bottom:

