- You are here:
- Home »
- Blog »
- Computer Technician Tools »
- CryptoPrevent – Protect Windows from Cryptolocker Infections
CryptoPrevent – Protect Windows from Cryptolocker Infections
Computer Technicians and System admins across the internet are hearing more and more about the Cryptolocker threat. If you havent heard about it, Cryptolocker is a nasty piece of ransomware that will seek out certain files on computers, attached drives and networks and encrypt them. Once it has finished encrypting the files, it will show a popup that tells the user that their files are encrypted and they have to pay a ransom to decrypt them before the 96 hour countdown completes. If the user doesnt pay the ransom during the countdown, the private key used to encrypt the files is destroyed and the users files become unrecoverable.
Nick from FoolishIT (creator of the popular tool “D7”) took the “How to prevent Cryptolocker steps” from BleepingComputers guide and turned them into a handy executable.
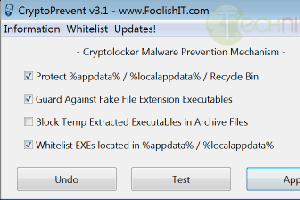
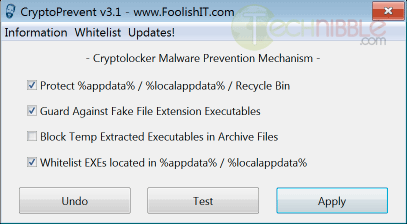
Basically, this utility artificially implants group policy objects into the registry in order to block certain executables in certain locations from running. For example, Cryptolocker drops a randomly named executable in the %AppData% directory and then runs it. This tool creates a rule (one of about 150) to stop executables running from this directory.
Please keep in mind that this tool is to be used before the infection. It will not help you if the computer has already been infected.
CryptoPrevent is free for both personal and commercial use but in order to make use of the automatic updates feature, it costs $25 USD. This cost is not required for usage and is entirely optional.
The application has many switches for automation and scripting purposes and comes with both a portable and installer version.
Screenshot
Downloads
Installer Version – 724kb
Portable Version – 407kb
Session expired
Please log in again. The login page will open in a new tab. After logging in you can close it and return to this page.

Do any of the major A/V companies have this sort of preventative restrictions?
I’ve found ESET is the only A/V that has been effectively blocking some of the new heavy hitters (like the Interpol virus).
But not sure how it stacks up against this form of attack.
(i.e., it’s hard to know what COULD have happened when you have proper A/V).
As far as I’m aware, none of the av’s currently have this form of preventative measures in place.
One thing to bear in mind though, is that IF cryptolocker is on a clients machine, and their AV removes the infection, then the ‘fee’ for decryption dramatically increases.
Have a look at https://www.technibble.com/forums/showthread.php?p=404095#post404095 for further details.
I’ve just been reading up a bit more on this evil scam (following worried emails from customers – no one hit – yet).
Seems my favourite a-v, Webroot Secure Anywhere, can do wondrous things…
https://community.webroot.com/t5/Security-Industry-News/How-To-Avoid-CryptoLocker-Ransomware/m-p/65059#M2423
and
https://community.webroot.com/t5/Webroot-SecureAnywhere-Antivirus/How-exactly-does-Webroot-allow-you-to-restore-files-encrypted-by/m-p/65147#.Uno4QhBurj9
Can this be safely installed on a server?
– 2003
– 2008
– 2012
From Nick Himself:
So the free tool will only protect them for a while til crypto is updated again. This could be a never ending battle. And I’m also interested in if the tool can be installed on a server. And if the tool causes issues. Once it’s uninstalled do things go back to the way they were.
It has an autoupdate option if you wish to pay for it. And as for whether it can run on a server, Nick says here.
So the free tool will only protect them for a while til crypto is updated again. This could be a never ending battle. And I’m also interested in if the tool can be installed on a server.
I believe a number of installers (e.g. Firefox) use these folders during installation. Is the “whitelist” checkbox in reference to these?
Correct. Nick said here:
@Soapy Buoy: All I can tell you is that I installed this on Win 2012 Essentials recently and it reported itself successful. There have been no performance issues that I’m aware of.
It’s my understanding that Cryptolocker chooses the files that it attacks using a list of file extensions. In a setting that has a relatively small number of files, would it make any sense to change the extensions on common file types (.doc -> .1doc for example) and then update the Windows file association list? New files could get renamed by a script job during the off hours. It isn’t perfect, but it does seem like it would limit your exposure. Or am I missing something basic?
would a real time file change monitoring software help? like nirsoft folderchangesview http://www.nirsoft.net/utils/folder_changes_view.html
from what i’ve heard cryptolocker does not show any prompt until it has finished encrypting all common data files which takes time. of course the question is would it be enough time to save your remaining files once you detect the encryption.
also unfortunately folderchangesview does not have an audible prompt.
I wonder if WinPatrol will alert of any changes CryptoLocker makes.
Thank you for sharing extraordinary informations. Your internet site is definitely cool. I’m impressed by the details that you have on this web site. It shows how effectively you understand this matter. Added this web-page, could keep coming back for more articles. You, my buddy, ROCK! %KW%
Madison http://be100loch.ru/user/kxbyxdxcfej/
I just wanted to send a quick word to offer you to thanks for some of the alternatives you are offering here. My important web study has by the end been determined with really great details to discuss with my family relations. %KW%
Ethan http://korea.peakbookmarks.com/story.php?title=tipps-zu-autoboxen-im-touran-von-volkswagen-1-4-united
Only want to comment you have an extremely ample site, I recognize the design it really stands out. %KW%
Elizabeth http://haplology.dividebookmarking.com/story.php?title=radio-klang-verbesserung-im-159-von-alfa-mit-neuen-tuerlautsprecher
It’s usually useful to study material from various other writers and use something from various other websites. I find some thing totally new and complicated on websites I stumbleupon on an everyday basis. %KW%
Sophia http://engineering.metasubmissions.com/story.php?title=bewaehrte-testsieger-zu-boxen-im-159-von-alfa-1-9-jtdm-16v-progression
Thanks a lot for discussing this with all people you truly recognise what you are speaking around! I’m impressed, I need to disclose. Rarely do I encounter a website that’s similarly educative and fascinating, and without a doubt, you’ve hit the nail to the head. Tyler http://www.article-marketing-solutions.info/authors/7566/Jack-Wylde