NETWizz
Well-Known Member
- Reaction score
- 2,005
Okay, it is NOT at all uncommon to get customers who complain that the traffic is slow at their sites, and they expect you to work some miracle of making a 3 mbps WAN circuit carry everything for 45 people...
The first thing you are going to need to do is figure out what is sucking up their resources.
To do this, you really need a managed router or switch that is the Gateway for the Subnet that is slow... You need to use sFlow to look at the traffic. Luckily, it's cake.
First you need some program that will run and collect the flows... I recommend Solar Winds Free Flow Analyzer:
http://www.solarwinds.com/freetools/real-time-netflow-analyzer.aspx
Once you get that up and running, just open it and the window will be blank... Now go to your router...
Here is the config:
ip flow-export version 9
ip flow-export destination <your IP here> 2055
interface SomeLink0/0
description Customer WAN facing Interface
ip address 10.1.2.3 255.255.255.252
ip flow ingress
!
interface SlowEthernet0/0
description Customer LAN facing Interface
ip address 192.168.1.1 255.255.255.0
ip flow ingress
!
You don't typically do in and out. Just do the in direction and if you don't get enough info, find the LAN facing interface and add the same command. The protocol is smart enough to figure out what comes in also went out.
You might also want to turn on SMTP for diagnostic purposes at least:
snmp-server community secretpub RO
***************************
The beauty is you don't have to do anything at all... It will simply populate in the software once it sees some flow data coming in.
Now click the little keys icon on the right and simply type your SNMP credentials (i.e. secretpub)
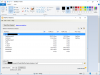
It will fully populate ALL interfaces, device type etc... It will look like this:
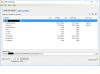
Now click on Start Capture... and wait about 5 minutes before trying to make sense of it. You want to grab enough traffic because it is hard to judge a congestion problem base don 10 seconds worth of flows.
Here our heavy-hitter is HTTP, TCP Port 80 (No surprise)...
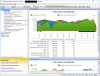
Now, it becomes clear where the worst part of the traffic is coming from:
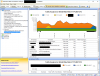
Now let's look at the conversation:
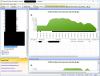
You could leave this running ALL day or even all week then come back and look at what is troubling your customer before coming up with an action plan if you want.
The first thing you are going to need to do is figure out what is sucking up their resources.
To do this, you really need a managed router or switch that is the Gateway for the Subnet that is slow... You need to use sFlow to look at the traffic. Luckily, it's cake.
First you need some program that will run and collect the flows... I recommend Solar Winds Free Flow Analyzer:
http://www.solarwinds.com/freetools/real-time-netflow-analyzer.aspx
Once you get that up and running, just open it and the window will be blank... Now go to your router...
Here is the config:
ip flow-export version 9
ip flow-export destination <your IP here> 2055
interface SomeLink0/0
description Customer WAN facing Interface
ip address 10.1.2.3 255.255.255.252
ip flow ingress
!
interface SlowEthernet0/0
description Customer LAN facing Interface
ip address 192.168.1.1 255.255.255.0
ip flow ingress
!
You don't typically do in and out. Just do the in direction and if you don't get enough info, find the LAN facing interface and add the same command. The protocol is smart enough to figure out what comes in also went out.
You might also want to turn on SMTP for diagnostic purposes at least:
snmp-server community secretpub RO
***************************
The beauty is you don't have to do anything at all... It will simply populate in the software once it sees some flow data coming in.
Now click the little keys icon on the right and simply type your SNMP credentials (i.e. secretpub)
It will fully populate ALL interfaces, device type etc... It will look like this:

Now click on Start Capture... and wait about 5 minutes before trying to make sense of it. You want to grab enough traffic because it is hard to judge a congestion problem base don 10 seconds worth of flows.
Here our heavy-hitter is HTTP, TCP Port 80 (No surprise)...

Now, it becomes clear where the worst part of the traffic is coming from:

Now let's look at the conversation:

You could leave this running ALL day or even all week then come back and look at what is troubling your customer before coming up with an action plan if you want.