britechguy
Well-Known Member
- Reaction score
- 5,099
- Location
- Staunton, VA
A few days back (during the "immense conflagration" period where my non-supported machine seemed to go off the rails with Windows 11) I decided during that time to download and unzip Nir Sofer's Nir Launcher. Windows Defender went wild, which was not totally unexpected, though I would have thought that ALL of his utilities would have been whitelisted on any antivirus by now (indeed, long ago, for that matter). When I decided to restore from a full system image backup I thought little more of it.
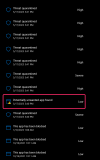
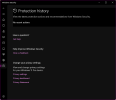
Well, today, I decided to try again, but this time I made a point of downloading the ZIP file to a thumb drive and keep all the action going on the thumb drive, looking to see if it might make a difference. It didn't. As the package unzipped I kept getting threat detection after threat detection, yet any time you'd open Protection History during the earlier ones it showed nothing, which is weirdness number one. Then, after a while, it was showing a long series of the detections, all of which had as part of the detection "HackTool," then, later on those disappeared (weirdness number two). There's no trace of any action having been taken by Windows Defender (weirdness number three).
I created a Feedback Hub issue, https://aka.ms/AAkup43, about the beginning of all this but that was submitted even before the mysterious disappearance of all the detections as though they never happened.
I do not believe my machine is compromised in any way, as this seems to be Windows Defender not liking some of the hacking techniques that the NirSoft utilities employ. But, I can't understand why it would present a long string (I think there were 18 or 19) of detections only to have those vanish from Protection History.
Has anyone experienced something similar or the same in the past with Windows Security/Windows Defender? I went from having the Defender shield with the red stop sign overlay straight back to the green checkmark overlay over the course of an hour or two without my having taken any actions and without any record of Defender itself having quarantined or otherwise acted on anything.
Well, today, I decided to try again, but this time I made a point of downloading the ZIP file to a thumb drive and keep all the action going on the thumb drive, looking to see if it might make a difference. It didn't. As the package unzipped I kept getting threat detection after threat detection, yet any time you'd open Protection History during the earlier ones it showed nothing, which is weirdness number one. Then, after a while, it was showing a long series of the detections, all of which had as part of the detection "HackTool," then, later on those disappeared (weirdness number two). There's no trace of any action having been taken by Windows Defender (weirdness number three).
I created a Feedback Hub issue, https://aka.ms/AAkup43, about the beginning of all this but that was submitted even before the mysterious disappearance of all the detections as though they never happened.
I do not believe my machine is compromised in any way, as this seems to be Windows Defender not liking some of the hacking techniques that the NirSoft utilities employ. But, I can't understand why it would present a long string (I think there were 18 or 19) of detections only to have those vanish from Protection History.
Has anyone experienced something similar or the same in the past with Windows Security/Windows Defender? I went from having the Defender shield with the red stop sign overlay straight back to the green checkmark overlay over the course of an hour or two without my having taken any actions and without any record of Defender itself having quarantined or otherwise acted on anything.