Velvis
Well-Known Member
- Reaction score
- 47
- Location
- Medfield, MA
a person reached out last week after they called the "Microsoft" number on a scam pop up. The scammers locked their computer and eventually asked for payments with a gift card at which point they called me.
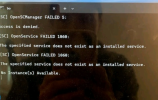
I was able to disable the PC lock, remove it and the remote access software they installed and removed all the PUP. I scanned it clean for malware and updated everything. Today they woke up to the computer with a command prompt open that I have attached and reads:
[SC] OpenSCManager FAILED 5:
Access is denied.
[SC] OpenService FAILED 1060:
The specified service does not exist as an installed service.
[SC] OpenService FAILED 1060:
The specified service does not exist as an installed service.
No Instance(s) Available.
Has anyone run into something like this before?
I was able to disable the PC lock, remove it and the remote access software they installed and removed all the PUP. I scanned it clean for malware and updated everything. Today they woke up to the computer with a command prompt open that I have attached and reads:
[SC] OpenSCManager FAILED 5:
Access is denied.
[SC] OpenService FAILED 1060:
The specified service does not exist as an installed service.
[SC] OpenService FAILED 1060:
The specified service does not exist as an installed service.
No Instance(s) Available.
Has anyone run into something like this before?