HCHTech
Well-Known Member
- Reaction score
- 4,432
- Location
- Pittsburgh, PA - USA
Almost all of my clients with servers are small, like less than 20 users usually. As a result, there is very little time advantage when I look at how to accomplish something. This means, I don't automate or script jobs that can also be done "manually". It also means I don't learn the scripting way, either.
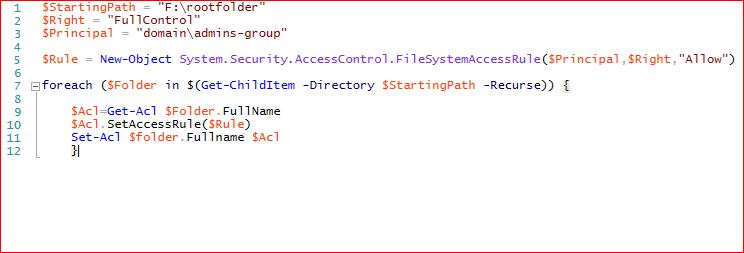
Here is today's example: I'm fixing a security problem at a client. Each domain user has a home folder on the network. Each user has a "Scans" folder inside of that home folder. They have a copier that can scan to each user's "Scans" folder, and the copier was setup to use the DOMAIN ADMIN account to access those shares : :
:
So I create a new limited rights user on the domain and I want to give that user read/write rights to each user's scans folder so I can then change the copier setup to use the new limited user for access instead of the domain admin.
Brute Force: I could just log onto the production server, locate each user's "Scans" folder and add that user with read/write permissions. There are about 20 users at this client, so this "brute force" way of accomplishing this task would take about 20 minutes.
He-man Scripting: I'm sure there is some powershell command with a FOR EACH loop that would do this job in about 15 seconds. But I guarantee you it would take me more than 20 minutes find the answer, mock it up, test (and inevitably troubleshoot problems) it so that it would actually work. In the end, I gave up and did this manually. It took a little bit longer than 20 minutes, but that was mostly because of interruptions. So I got the task accomplished, but I'm also disappointed in myself again for NOT doing something the "right way".
If I had 1000 users, there would be no choice but to figure out how to script the job. If I only had 5 users, I would do it manually every time. 20 users is somewhere in the middle, so I don't feel too bad, but I'm still disappointed I guess.
How would YOU have done this job?
Here is today's example: I'm fixing a security problem at a client. Each domain user has a home folder on the network. Each user has a "Scans" folder inside of that home folder. They have a copier that can scan to each user's "Scans" folder, and the copier was setup to use the DOMAIN ADMIN account to access those shares :
So I create a new limited rights user on the domain and I want to give that user read/write rights to each user's scans folder so I can then change the copier setup to use the new limited user for access instead of the domain admin.
Brute Force: I could just log onto the production server, locate each user's "Scans" folder and add that user with read/write permissions. There are about 20 users at this client, so this "brute force" way of accomplishing this task would take about 20 minutes.
He-man Scripting: I'm sure there is some powershell command with a FOR EACH loop that would do this job in about 15 seconds. But I guarantee you it would take me more than 20 minutes find the answer, mock it up, test (and inevitably troubleshoot problems) it so that it would actually work. In the end, I gave up and did this manually. It took a little bit longer than 20 minutes, but that was mostly because of interruptions. So I got the task accomplished, but I'm also disappointed in myself again for NOT doing something the "right way".
If I had 1000 users, there would be no choice but to figure out how to script the job. If I only had 5 users, I would do it manually every time. 20 users is somewhere in the middle, so I don't feel too bad, but I'm still disappointed I guess.
How would YOU have done this job?