- You are here:
- Home »
- Blog »
- Computer Technician Tools »
- How To Recover Email Passwords From Any Email Client With MailPassView
How To Recover Email Passwords From Any Email Client With MailPassView
We’ve all been in this familiar situation before: a customer calls you to have their old computer data migrated to a fresh new system they just purchased. All the easy stuff transfers just fine, but then you realize that Outlook or Thunderbird need to get moved over. Getting the email client data files moved across machines is fairly simple, but then the tricky part hits you. The customer has a mixture of 5 different POP and IMAP accounts they connect to, and expect you to replicate their setup in 1:1 fashion on the new machine. They have no clue what passwords relate to any of the accounts. Where to next?
Enter one of my favorite gems when it comes to email client migration. The program is a freeware utility called MailPassView and it is developed by the excellent people behind the website NirSoft. There’s not much that needs to be said about system requirements because it’s likely the most liberal program when it comes to operating system compatibility. It works on every version of Windows since 98, and I’ve never experienced any issues with x64 flavors of any OS, either. It also, quite remarkably, supports nearly every email client under the sun (except for Lotus Notes perhaps). The most common ones supported that technicians will encounter include Outlook 2000 and up, Outlook Express, Windows Live Mail, Windows Mail (from Vista), Eudora, Thunderbird, and even helper programs connected to email accounts like Google Notifier. That’s an impressive spec sheet if I’ve ever seen one.
How does it work? Here are the simple steps for using the program in its most basic form:
1) Download MailPassView here: http://www.nirsoft.net/utils/mailpv.html.
2) Launch the program (for zip users, merely launch the sole exe file in the extracted folder).
3) The program will launch and merely display all available account details from every email client on the system. You can “refresh” the program if you feel it didn’t grab all proper settings on the first run.
4) You can either manually copy out your account details, or better yet, use the simple “Save” floppy icon on the left hand side of the toolbar to save a text file of your results.
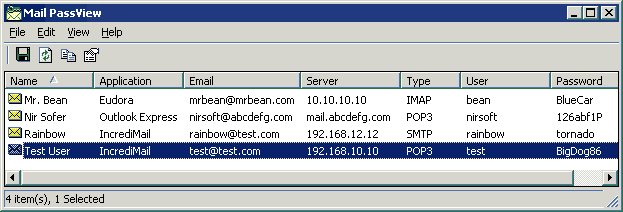
It’s that easy. The program is super simple to utilize, but it comes in handy for those very situations where a customer just can’t remember their account credentials for the life of them. MailPassView doesn’t stop at passwords only. It also provides full POP/IMAP/SMTP settings for any email accounts it can sniff out. The full list of details it can weed out includes:
- Email addresses (full)
- Server addresses (incoming & outgoing)
- Server ports (incoming & outgoing)
- Email passwords
- Password strength
- User profile names (most pertinent for Outlook setups)
In all, MailPassView is an excellent tool for any computer technician that is tasked with migrating an email client setup for their customer. I’ve used the program countless times with great success. If your email client happens to not be supported, they even offer an alternative utility called SniffPass that claims to be capable of, well, “sniffing” out passwords traveling over your network adapter. I’ve never had a need for SniffPass personally, but I’m sure it works as solidly as MailPassView.
If you have any comments about MailPassView, please feel free to post them below.
Session expired
Please log in again. The login page will open in a new tab. After logging in you can close it and return to this page.

Have used this tool for quite some time and it’s been a lifesaver many times. Not only for when the customer can’t remember his password, but also when the customer’s email address domain and the pop/smtp server’s domain are different (very common with custom email domains).
Do watch that some Anti-virus solutions (corporate McAfee and Norton especially) will mark this as a spyware program and delete it upon downloading. While the A-V products are technically right, this program is work its weight in gold in a Outlook heavy office that isn’t using Exchange.
Avira marked this as unsafe so it was not downloaded. What a shame as it does seem to be just what is needed.
Same problem here. I tried to use it at work and our AV program not only stopped it, it removed it from my flash drive. If anyone knows a way around that, I’d like to hear it.
I’ve found that I can often run MPV in safe mode to get past the AV programs removing it or disabling it.
With some AV programs, you can whitelist MPV. Most of the time, it gets sent to quarantine, so you can restore it from there.
Otherwise, the only option is to uninstall the AV program before using MPV, which is not a great thing if you aren’t reinstalling Windows.
What about the case when you simply can’t get into Windows?
To get into windows use konboot. There is an article about it on here, go back a few pages.
Thanks for that, Jim. I’ll give it a go.
I wonder if it’s similar to Hiren’s Boot CD which allows you to load “mini xp”.
No, konboot is not similar to MiniXP. MiniXP is a miniature version of Windows XP on a LiveCD. Konboot actually allows you to access the Windows install on the machine but without the need for user passwords.
Due to its password revealing nature, some Antivirus products see MailPassView as a hacking tool.
Avast is a Nir Sofer friendly AV.
I’m surprised that so many people won’t run a tool simply because it shows up as spyware on a scan. Shame on those of you! Many good technician tools show up as spyware or malware due to the things that they can do, such as reveal or change passwords, but are legitimate. If you are that concerned about the legitimacy of the software – and rightfully you should be about anything you download – research it. Search engines are your friend!
If I chose not to run a program simply because it was labelled as spyware or malware of one kind or another by an antivirus program, I wouldn’t have a few of my most useful tools. Technically, this program is spyware, but the good kind when used as intended! All of you who are complaining about this ought to follow a simple procedure, which I have listed below. I’m surprised you haven’t, especially the first one!
1. Use a search engine; research the program. Is it legitimate or malicious? Don’t just trust the first source you run across. Do some real research. Some forums have more knowledgeable people on them, but some do not. If at all possible, see what IT professionals or websites such as MajorGeeks say, as those are more reliable sources than a random forum.
2. If the program is safe, download it from the source, not some random website with a download link, just to be safe. If the software does not have a direct download, use a mirror site that is listed on the source’s website. Many programs are available on sites such as CNET Downloads, which is usually safe, too.
MPV sometimes has problems with Outlook on 64bit systems. I have had it report blank passwords when there are clearly passwords stored on 64bt Win7 and Vista with Outlook 2010. Your mileage may vary. Otherwise it is an essential too in the tech’s armory.
For some reason the link listed for this product does not work. Does anyone have an idea where I can get the download for this? Thanks
I just checked my links and they all work. Please try again, or disable your AV software. ESET NOD32 v6 was picking up the downloads as infected (mistakenly, mind you).
Great tool…worth a try. Very handy for computer repair technicians. What about when win it’s not loading or your hard drive it’s busted? Any data recovery programs that will look for user email accounts and their. Passwords?
Great article, that’s why we following your posts huys.
Thanks.