- You are here:
- Home »
- Blog »
- Manage Your Computer Business »
- Bypass Windows Logons with the Utilman.exe Trick
Bypass Windows Logons with the Utilman.exe Trick
Utilman.exe is a built in Windows application that is designed to allow the user to configure Accessibility options such as the Magnifier, High Contrast Theme, Narrator and On Screen Keyboard before they log onto the system.
This was designed to help people who are hard of sight, hearing or mobility to log onto Windows themselves without the need of outside help. Its a great feature for disabled people but it opens up a security hole that we can take advantage of to bypass Windows logons.
Bypassing the Windows logon comes in handy if our clients have forgotten their logon password, their user profiles were corrupted or malware was interfering with the system before login.
This works because the user can trigger Utilman by pressing Windows Key + U before Windows logon. This will load up the Utilman.exe executable which resides in the Windows\System32 directory. If you swap the Utilman.exe file with something else like cmd.exe, you have access to the command prompt running SYSTEM privileges. SYSTEM is an account with the highest possible privileges on Windows which similar to the root account on Unix systems.
Here are the step by step instruction on how to do this.
WARNING:
You can do a lot of damage to a system if you dont know what you are doing. Technibble accepts no responsibility if something goes wrong.
First of all, we will need a way to access the file system to swap out Utilman.exe with something else like cmd.exe. There are a few ways to achieve this:
- Remove the operating system hard drive from the target system and slave it into another system with a working operating system. From there you can swap out the files on the slave drive
- Use a Boot CD like UBCD4Win and use the file management software there
- Use the Windows Vista or 7 DVD
In this example we will be using the Windows 7 DVD. To begin, boot from your Windows 7 DVD and when you reach the first screen asking about the language, currency and keyboard format, Click Next.
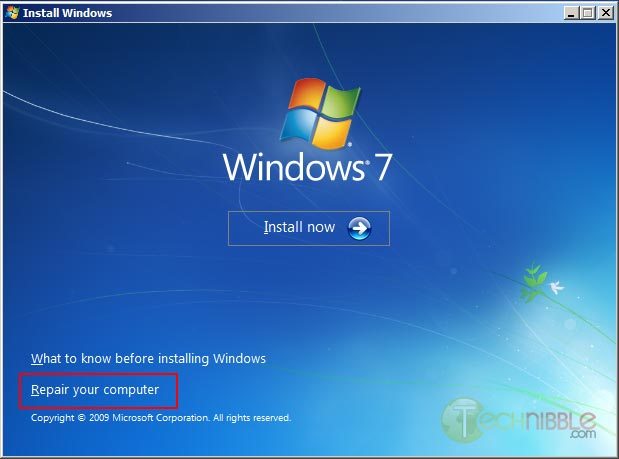
On the next page, down in the lower left hand side, click on the “Repair your computer” link.
Next, select the “Use recovery tools that can help fix problems starting Windows. Select an operating system to repair” option, choose an operating system from the list and Click Next.
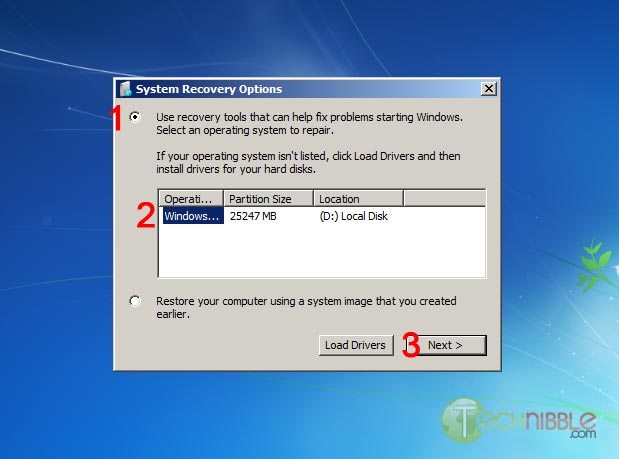
You will now have an option to “Choose a recovery tool”. Select Command Prompt.
You should now have a Command Prompt Window open. Type in the following commands:
C:\
cd windows\system32
ren utilman.exe utilman.exe.bak
copy cmd.exe utilman.exe
This will navigate to the system32 directory, rename utilman.exe to utilman.exe.bak, make a copy of cmd.exe and name it utilman.exe.
Remove the DVD and reboot the system.
Once the computer boots up normally, press the key combination Windows Key + U and you should get a Command Prompt. If the Command Prompt doesnt appear, press Alt+Tab as the Command Prompt may appear behind the Logon screen. From here, you can run many (if not all) of the commands you can normally use in Command Prompt.
Resetting an Existing Users Password
WARNING:
If you reset a users account password. This will permanently lose access to the users encrypted files. Be sure to back these up.
To reset an existing users password, we need type the text below. In this example, we will be changing JohnDoe’s password to “hunter2”.
net user JohnDoe hunter2
You should be able to log in with this new password straight away.
If you dont know what the username on the system actually is, you can see a list of the users by typing:
net user
Creating a New User Account
To create a new user account in the Command Prompt (Username: NewGuy. Password: abc123), and add them to the Administrators usergroup type:
net user NewGuy abc123 /add
net localgroup Administrators NewGuy /add
Again, you should be able to login straight away with this new account.
Reverting Changes
To restore utilman.exe, in the Command Prompt type in:
C:
cd windows\system32
del utilman.exe
ren utilman.exe.bak utilman.exe
Then reboot the system.
To remove the new user account you just created earlier, type in:
net user NewGuy /delete
That’s all there is to it.
Thanks to MobileTechie for mentioning this trick.
Session expired
Please log in again. The login page will open in a new tab. After logging in you can close it and return to this page.

Nice! I remember doing this with scrnsave.exe in the WinXP days.
Nice, nice.
BUT: For years I have not seen any Win system with a “Windows CD”. So why do we keep mentioning it as a tool of choice?
Well, Maybe down under you still get them?
Okay, I do have a bunch of UBCD4Win CDs and similar ones, no problem to get it done.
yes we do still get them. Kon-boot seems to be the right tool for this scenario according to the other techs on the forum.
Hack into windows by first logging in with admin privileges. Genius!
I’ve been doing a similiar trick for ages with Windows 7. Sticky keys. Pressing shift 5 times opens SCUTIL.exe, I just boot into Windows PE, move the original and then overwrite it with cmd.exe. Works perfectly :)
Pardon me… but this Utilman.exe rigamaroll seems like a very goofy way to go… pretty ridiculous! Pulling the OS hard drive, etc. When you can just purchase Spotmau PowerSuite 2012 for $39.95 and have the password reset plus 40+ other utility functions available to you. Total time under 1 minute and works everytime. If a person is going to be a PC Tech and can’t spend small amounts of money for real tools. Then maybe they shouldn’t be a PC Tech. To “neF” all I have to say is you can log into admin IF you have the admin password. Genius! Yes, a lot of times there is no Admin password. But alot of times there are… and no one seems to know it. So, your comment seemed rather inexperienced.
Well, someone is a debbie downer. You can use a disc to do it, no drive pulling necessary. Admin password isn’t as necessary since the cmd.exe is running as SYSTEM, as stated in the above article.
I’m guessing you glanced over it and just read the comments more to see who to make fun of? Or just want to plug a product? Being able to do something like this in front of a customer makes it seem more impressive anyways(as most CLI stuff does)
Is this for an unlimited, technician license?
Bryce, this seems to be quite a tedious process to access a password protected Windows when there are live disk tools available to do almost the same thing. Offline NT Password and Registry Editor is my tool of choice and has a CLI which somewhat disguises the operation from anyone looking over your shoulder. PC Login Now has wrapped the same operation into a nice GUI.
To pull the drive and manually edit the registry as you suggest is like learning locksmithing to get into your front door when there is a backdoor key hidden under the mat.
I like. Very nice. Thanks!
On the Cmd you can also enable the administrator by this step
net user Administrator /active:yes
to deactivate to this administrator do this
net user Administrator /active:no
And also replace your users password like this
net user TheUserName *
re-type the password
re-type the password again
After changing the you have just replace this the password.
There is another great method to reset windows password,that’s use Windows Password Reset.
Here are 3 steps:
Step1:Download and install Windows Password Reset from http://www.windowspasswordresest.net
Step2:Burn Windows Password Reset ISO file to CD/DVD,or USB.
Step3:Put in your newly created CD and remove your Windows Password.
As someone referred before the best and fastest way do do it and impress a customer is to use Kon-boot and the usb version if possible, in the password part you ask the customer to look the other way cause it’s a “special password mode” “techies magic” your gonna use and that will impress any customer and if the customer so wants from cmd line and inside their own session they change their own password with the net user command, i bet that customer will always come back for your support.
Bipc – Portugal – Hello to you all :)
I find Ophcrack works for this most of the time. A lot easier.
I second using Offline NT Password and Registry Editor or Ophcrack. Both are free and a lot quicker than going though this whole process. It’s an interesting bit of geek knowledge but more time equals less money when running a business.
These people subsequesnt to my comment all made some great points and provided good info on other tools. I wasn’t trying to be a debbie downer Jamie. I was basically trying to say what Atlantic Jim so eloquently did. I’m glad by knocking something a bit that all these other people stepped up and made contributions on the subject/problem solution. That’s what is great about this forum. I was not plugging a product. I forgot to mention that there were 4 or 5 free software solutions. But the guys came up with ones I did not know about that were really great! I merely pointed out a Cadillac solution that would give you across the board solutions to many other problems. I just don’t thinking pulling out a hard drive in front of a customer is impressive at at all! Solving the clients problem in the fewest steps possible, in a minute or two… is a better demonstration of knowledge and skill. Of course by pulling the HD you could show them all the dust bunnies and cobwebs in their machine and ask to borrow their vacuum cleaner. Then there is the slight possibility that by opening their PC and removing their HD and doing the little hacking that there PC may not boot again. You could cause other internal problems (MB damage, static discharge because you forgot to ground yourself first or discharge any static electricity in you by first touching the power suppy and then for good measure pressing the power on button for a few seconds before proceeding. I know that any chance of problems would be very slight for a trained PC Tech. But my point is why even go there! When you could solve the problem from the mouse and keyboard. Now let me say that the author that posted this article “Bryce Whitty” seems like a sharp and knowledgable guy. He has demonstrated his knowledge of Windows and that he can come up with original solutions. I was not knocking him
But again … not pulling out the hard drive.
This is all done without pulling out the hard drive.
I’ve also used registry hacks to trigger the OOBE “wizard” where the wizard pointer in the registry was replaced with cmd.exe. Konboot and Offline NT Password and Registry Editor replaced this approach for me.
With this approach won’t Windows File Protection kick in and replace Utilman.exe with the backup copy?? Or does that only trigger after login? I’ve never really played much with this approach so I’m unsure when the WFP feature kicks in, if at all in this scenario.
Great points altogether, you just received a emblem new reader. What may you recommend in regards to your put up that you just made some days ago? Any certain?